Top 5 Network Monitoring and Management Priorities for 2020: What 300 IT Leaders Had to Say
2019 has been a crazy-busy year at Gigamon. We expanded our capabilities in private and public clouds, went deep into container visibility and launched Gigamon’s best-selling application to date, Application Intelligence.
As we look ahead to 2020, it is important for us to remain focused on the networking challenges our customers and the wider IT community face every day. The more we understand their network management and monitoring priorities in 2020, the better equipped we will be to help them reach their objectives. With this goal in mind, we began an effort in September to benchmark the current networking landscape and learn more about organizations’ expectations and priorities for 2020.
We partnered with Gatepoint Research, an independent research firm, to survey organizations — both customers and non-customers — across a broad range of industries.
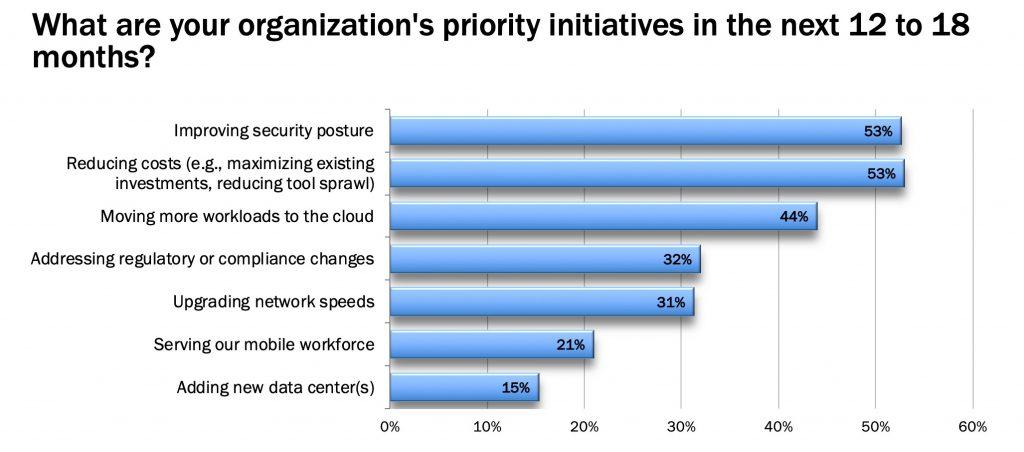
In the end, more than 300 IT leaders heading up Network Operations and Information Security at their organizations volunteered responses. (A big thank you to everyone who participated!) Here’s what they reported as their top priority initiatives for the next 12 to 18 months:
5. Upgrading Network Speeds
Coming in at number five is network speed upgrades. While this initiative appears last on the list, 31 percent of respondents selected it — that is significant. This is not too surprising since most networking professionals are accustomed to organizational growth and new business demands making network upgrade projects a fact of life.
When planning a network upgrade, it is sometimes easy to overlook the impact that additional network capacity will have on the volume of data that network management and security tools must contend with receiving. When data volumes spike, it can be a challenge for existing tools to keep pace. Critical tools that rely on network traffic visibility to function may experience speed incompatibility and performance issues if their needs aren’t assessed as part of the upgrade plan.
Without the ability to manage and control the traffic that existing tools receive, so they are not overwhelmed, organizations may find themselves overextending their budgets with large unplanned expenditures to maintain the performance of their existing technology stack, a cycle that may repeat with each subsequent upgrade.
4. Addressing Regulatory or Compliance Changes
As the number of highly publicized breaches rises, regulatory bodies are demanding increasingly stringent technical requirements to improve privacy and security, making this initiative top of mind for 32 percent of IT leaders.
New compliance and data privacy directives are introduced each year, and existing regulations often evolve in response to a changing threat landscape. For example, the EU General Data Protection Regulation (GDPR) is now active, and, beginning in January 2020, the new California Consumer Privacy Act (CCPA) will take full effect as the U.S. begins taking a stronger stance on protecting citizens’ data being processed by private parties.
Furthermore, the ability to detect and contain breaches before bad actors can explore a network and compromise sensitive customer and company data is essential to avoiding both hefty fines and reputational damage.
Without insight into all traffic, including east-west and cloud traffic, it can be difficult for organizations to maintain a strong security posture and prove compliance on an ongoing basis and during compliance audits.
3. Moving More Workloads to the Cloud
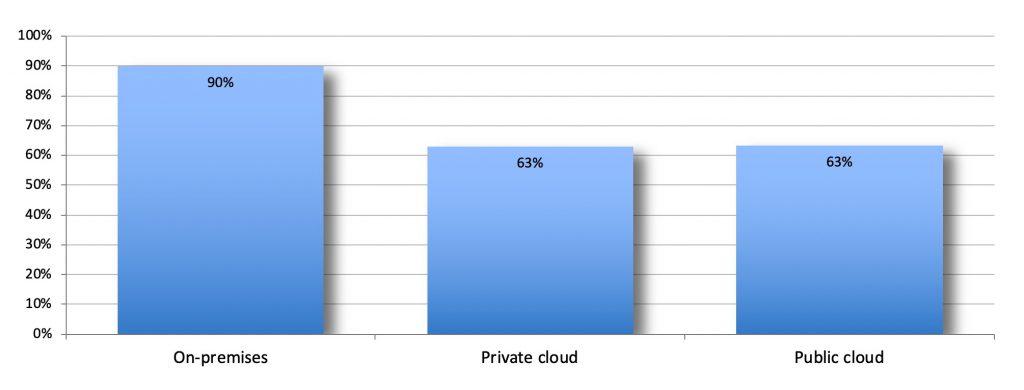
Though survey respondents reported that on-premises infrastructure is still the most common environment used (90 percent), private and public cloud environments are catching up, with over 60 percent of respondents saying that they use either or both.
With the cloud’s scalability and flexibility, migrating additional workloads to public and/or private clouds just makes strategic sense for many organizations.
However, this move has obvious implications for the organization’s security models and how IT teams can continue to support applications and services running in cloud environments.
Whether they are managing a cloud or a hybrid environment, it’s critical for IT leaders to begin 2020 with a plan for how they will achieve visibility into both private and public cloud workloads. Despite the convenience of the cloud, without visibility across all their environments, IT and security teams and tools will face blind spots that put their organization at risk. (Spoiler alert: 2020 will be the year of the cloud for Gigamon. Stay tuned to see what our customers will be able to do!)
1 and 2 (We Have a Tie at 53 Percent Each)
Reducing Costs
The benefits of fast networks come with some whopping costs. As business needs change and the volume of network traffic increases, organizations are often forced to upgrade or add additional tools, driving up annual hardware and software budgets in what can seem like a never-ending cycle.
It’s only expected to get worse. In the 2019 ESG Economic Validation Report, the research firm Enterprise Strategy Group found that 80 percent of the data that exists now was only created in the past 24 months.
To extrapolate forward, that means that today’s data will only account for 20 percent of the data in 2021!
Even if organizations don’t yet know the exact numbers, most see the growth trend going up exponentially and are looking for ways to get more out of existing tools and resources in 2020 with hopes of realizing cost savings (or at least not blowing their budgets).
Improving Security Posture
Again, no one wants to be the headline of the next news cycle. With business executives increasingly concerned about data breaches, security is also top of mind for more than half of those surveyed.
In another report, 78 percent of organizations estimated that they experienced a successful cyberattack in 2019. IT leaders and company executives are right to consider security a priority.
When it comes to improving security posture, gaining better visibility is the first step organizations need to take. Security tools that rely on network data to perform their respective functions are ineffective at protecting your organization if they don’t have access to full-fidelity data and visibility across all areas where unusual or malicious activity can occur.
Gearing Up for 2020?
Managing your network in today’s increasingly complex environments comes with unique challenges. Just mirroring the right traffic information to the right security tools or delivering reliable data to internal teams is difficult. Cloud traffic and encrypted traffic, in particular, often creates significant network blind spots, creating unforeseen risk.
Adding more hardware or software may help when tools are overloaded, but this comes with increased costs, downtime and complexity. How can organizations make network monitoring and management work better for them in the new year?
Gigamon is here to help your 2020 network initiatives succeed. From our unique vantage point, between the infrastructure layer and your tools, we give your teams and tools the pervasive visibility they need by collecting network data-in-transit across physical, virtual and cloud environments, optimizing and transforming this data to comply with policies and then automatically delivering the right traffic to the right tools. This approach greatly simplifies network management and lets you get the most out of your technology stack of today and tomorrow.
Interested in reviewing the full research report, “Approaches to Network Monitoring and Management”? Download your free copy today.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Networking group.
Share your thoughts today