NCSAM Week 2: Super Dave
Editor’s note: Too often your weakest security link is a human, who we like to call Dave. He’s doesn’t mean to be a threat, he’s just a person going about his day. For National Cybersecurity Awareness month get tips for promoting good security practices with your own employees like him.
Before we get started, I’m going to need all executives, managers and general security personnel to turn around for a second while I have chat with our users. Go ahead, we’ll be right with you — just hang tight. Also, earmuffs. No eavesdropping. Good? Good.
Hello, humans. My name’s Danny and on behalf of all the people currently pulling a Blair Witch in the corner, I’d like to apologize to you. We screwed up. In our pursuit of securing all the things, we have failed to secure our most valuable resource: you.
It’s a whole teach-a-person-to-fish type deal, but let’s try to figure this out. Also, if you ever wanted to vent about your security department, now’s the time, while their attention is elsewhere. Don’t worry, I gave them Nintendo and juice boxes filled with Scotch. They’ll be okay.
October is National Cybersecurity Awareness Month and marketing, wisely or unwisely, put me in charge of the second blog in our Cybersecurity Awareness Month series. The theme is “Don’t Be Dave.”
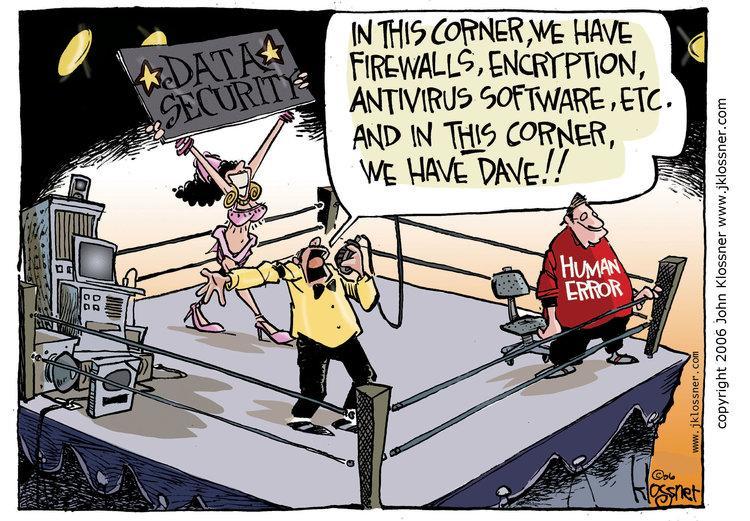
The overall theme being, “Dave” is our archetype of a user who’s able to circumvent all the blinky boxes we spend big money on to secure a network. Dave clicks the links, sticks the thumb drives in, surfs to polluted websites, so on and so forth.
First off, apologies to all the literal Daves out there. I guess we had to name the example something and one of your ilk must have annoyed the cartoonist that day. I’m sure most of you are lovely people.
Granted, sometimes “Dave” really is just a jerk, but most times we, the people who are paid to care about such things, just haven’t done enough to make Dave feel like he’s got some skin in the game. He hasn’t bought into our core security strategy because there’s nothing in it for him, or so he thinks.
When I was asked to write this blog, the first person I thought to chat with was my pal Jayson E. Street, VP of InfoSec at SphereNY. Jayson is a world-renowned social engineer (he hacks the humans) and someone whose job it is to test the human element of an enterprise.
We had been on the phone for about five seconds before he informed me that he’s already done a talk on this very topic. When you have a moment, I highly recommend watching the recording of that talk, a keynote address at LASCON 2018. I swear it’s not too technical (read: boring) and, more importantly, it’s a terrific translation from us security people to you, the people we’re sworn to protect and educate.
As Jayson and I spoke, he hit on the crux of the issue right off the bat.
“Why is it that we as an industry always default to breaking our users down when, instead, we should be building them up? We need to stop trying to look at technology to secure humans and look more to those humans to help secure our technology. Users are an asset. If you see them as a liability, it’s because you made them that way. Every single person from the CEO to the mailroom intern is part of your information security plan.”
He continued:
“When you hire a truck driver for your company, you teach them to do what’s required so they don’t lose their job. Don’t speed, don’t text and drive, don’t run over old people. Those employees will do their darnedest to not get into accidents because they could lose their jobs. If we’re not applying the same methodology to security training, teaching these users that they could lose their jobs, we have failed them.”
Sometimes, even we as security professionals need reminding that things intuitive to us are completely alien to the users we support. What we see as security in depth, regular users see as inconvenience. The difference being, we’ve seen the worst that can happen from inattention to security. Our jobs literally depend on us being paranoid. Melanie in purchasing just gets an email that a virus was detected on her machine. Again.
Blogs like this should always close with some kind of actionable intelligence. Something you can take away and put into practice. You can read a hundred different blogs this month that will drill home the same pieces of advice. Don’t click links in email, use two-factor authentication, don’t fall for phony phone calls.
My goal here is a little deeper: empathy. Empathy to not only make you aware that security is your responsibility but also to hold us accountable when you simply don’t know something and we’re not being very helpful assisting you with understanding.
What does every article about every huge breach have in common? TJX, Heartland, Hannaford, Target, Home Depot — they all ended up just fine. Stock? Barely dipped. Reputation? Washed clean from a heavy rain like chalk on a sidewalk.
One wonders, then, where’s the incentive to get us to get our users to care about how they conduct themselves online? That’s actually a serious, non-rhetorical question. I’m asking each and every person reading this blog to respond to us in the Gigamon Community’s Security group. We all need to believe we’ve got skin in the security game. We want to be better educating our clients, helping them reach their potential as Defenders of the Defenses.
Get more perspectives for encouraging employees like Dave to practice better security hygiene.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today