Security Professionals Share Concerns, Plans in 2019 Cyberthreat Defense Report
Hot off the presses is CyberEdge Group’s “2019 Cyberthreat Defense Report” (CDR), which compiles and interprets the aggregated insights of 1,200 IT professionals across 17 countries and 19 industries. The report reveals what your IT peers are thinking and doing as it relates to threat trends and cybersecurity. Topics range from what technologies they’ll be investing in next year to what’s been keeping them up at night.

While the Cyberthreat Defense Report is editorially independent, Gigamon is a platinum sponsor and is happy to offer you access to the research. You can download the full report here, peruse an executive summary or keep reading for a quick summary of its findings.
Notable Survey Findings
To start, the report calls out some notable findings around the greatest perceived cybersecurity threats, budgets and planned purchases, and barriers to effective cyber defense:
- The top obstacle to achieving effective threat-hunting capabilities is the difficulty organizations have implementing or integrating related tools
- Of 11 categories of cyberthreats, malware is the greatest concern for responding organizations, followed closely by phishing and ransomware
- Advanced security analytics tops the list as the number one security technology planned for acquisition in 2019
- On average, security budget has grown to 12.5 percent of an organization’s overall IT budget
Interesting. Let’s go deeper.
Cyberthreat Highlights
While the previous CDR from 2018 found the first-ever year-to-year decline in successful cyberattacks, the trend did not pan out, with 78 percent of this year’s respondents reporting a successful attack against their organization (up from 77.2 percent in 2018). Telecom and technology (81.2 percent), education (80 percent) and retail (79.2 percent) were most affected, with healthcare attacked least often (69.1 percent).
Meanwhile, ransomware such as WannaCry is still making the rounds, and according to the 2019 CDR the news isn’t good. While the percentage of affected organizations increased only by one percent (56.1 percent this year), the percentage of organizations that actually paid ransoms has soared from 38.7 percent in 2018 to 45 percent in 2019. What’s more, 38.8 percent of those that paid a ransom still lost their data. (19.2 percent of respondents refused to pay, and lost their data that way.)
Wanted: A Better Way to Decrypt Traffic
It’s interesting to see that SSL/TLS decryption has finally hit a saturation point, with 59.4 percent reporting this capability in their current security deployments and 29.8 percent declaring their intention to acquire it (see page 24). However, the “perceived adequacy” of these tools is low, with 73.9 percent agreeing that “efficiently decrypting network traffic remains a challenge.” Moreover, hard-to-monitor blind spots persist around the infrastructure.
As a result, the CDR suggests that TLS decryption efficiency and centralization will only grow in importance as encrypted traffic workloads continue to grow. Centralized SSL/TLS decryption solutions, such as those offered by Gigamon, can help ease these growing pains by observing all SSL/TLS traffic in a central location and only passing relevant decrypted traffic to specific security tools, reducing overall load on the security infrastructure.
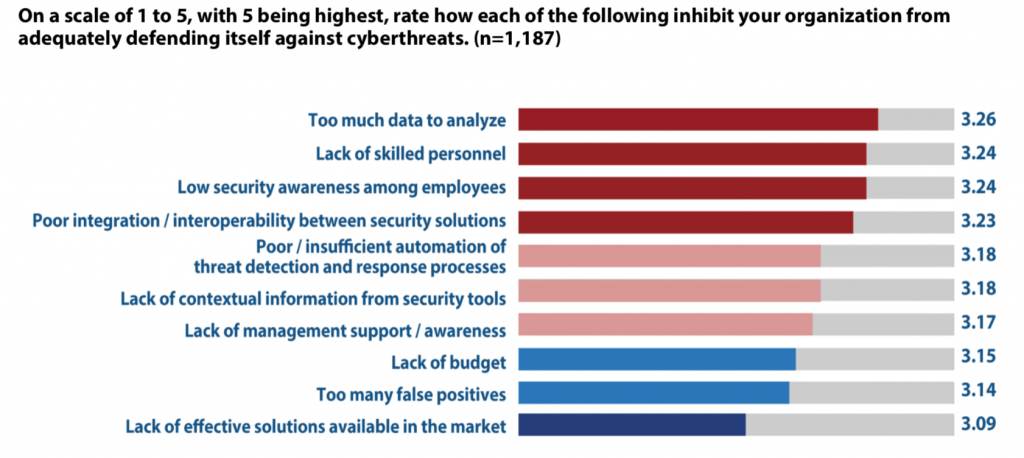
On a related tangent, having too much data to analyze is the number one factor respondents cite that prevents their orgs from adequately defending against cyberthreats (see Fig. 1). It’s the ever-present needle in the haystack problem and a frequent thorn in IT’s side. Again, this is another area where centralized Gigamon-style solutions are relevant, given their ability to quickly assess large amounts of incoming data and route it only where it’s needed, saving tools from analyzing irrelevant noise.
Get the Full Report
Want more insights and analysis? You can get a copy of CyberEdge Group’s 2019 Cyberthreat Defense Report right here or register for the webinar.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today