Securing Resilient Networks
Updated October 28, 2021.
Your network is the lifeblood of your business. It’s how customers reach you. It’s how you process orders. It’s how you manage employees. For this reason, the network must be both resilient and secure. Too often, these qualities are at odds.
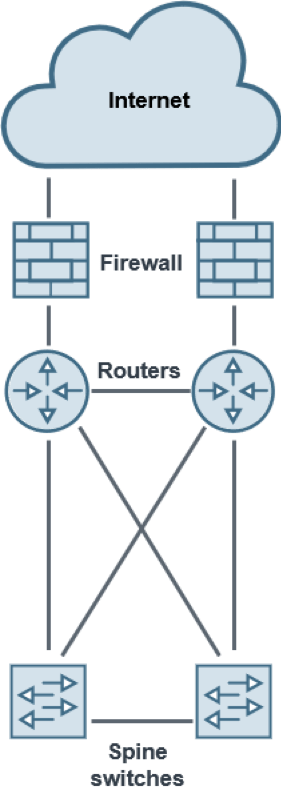
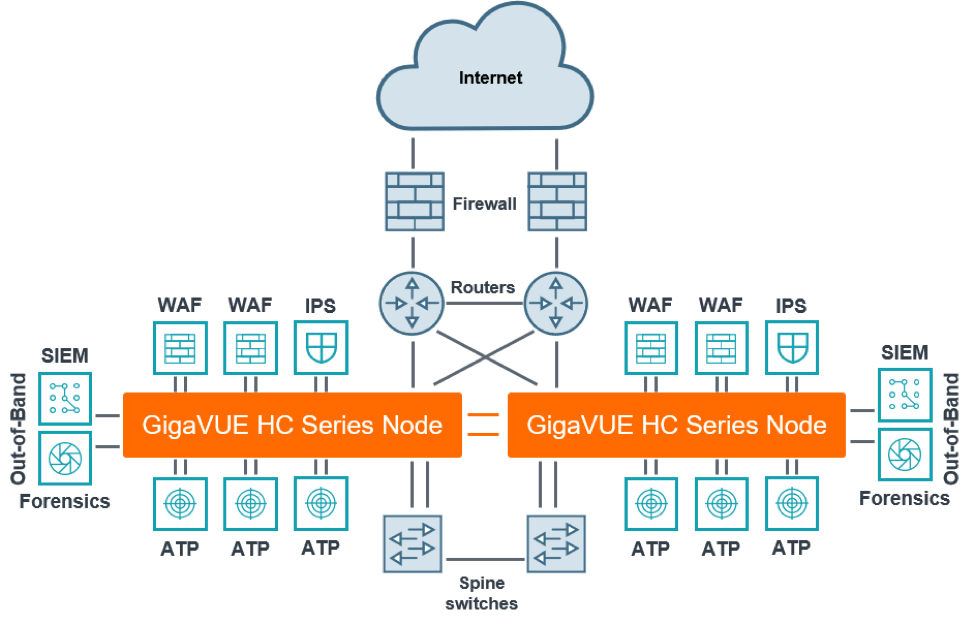
The most common way to achieve network resiliency is with a dual-path or bow-tie architecture, whether in an active-active or active-standby configuration. Instead of just a single path for traffic to flow — where a single point of failure can cause an outage — there are two or four paths traffic can take.
When one path fails, such as a switch or router port going offline, the network will fail over to another path. Routing algorithms can even monitor congestion and direct traffic to minimize latency and maximize network and application performance.
Unfortunately, more paths create more opportunities for threats to infiltrate your network and exfiltrate your and your customers’ data. This type of architecture was designed for network resilience, not cybersecurity, so security solutions require special consideration.
The increased number of paths increases the number of ports and throughput capacity required on security tools, making them more expensive. For out-of-band security solutions such as intrusion detection systems and SIEM, these paths must be tapped and consolidated through Gigamon Visibility Fabric™ and Gigamon Visibility Platform. Inline threat prevention tools, such as IPS and WAF, face further challenges.
Sending redundant paths through the same inline threat prevention tool introduces a single point of failure and breaks the redundancy of the network architecture, compromising your network resilience. On the other hand, deploying separate tools on each path becomes very costly, very quickly. Most challenging of all, packets within a single session, such as ingress versus egress traffic, may follow different paths within active-active networks. This asymmetric routing prevents the inline tool from seeing all the packets of a session, and this missing data means it can’t detect or block threats.
What’s needed is a security architecture specifically designed for redundant network paths and network resiliency. Gigamon Resilient Inline Protection (GRIP™) deploys an HC Series node on each side of an active-active or active-standby network and then interconnects the nodes with a dedicated link.
GRIP distributes session traffic across both nodes such that any inline or out-of-band security tool connected to either node receives all the packets of a session, even when asymmetric routing is occurring. Furthermore, the tools on the standby side can be utilized so that they are not sitting idle; this maximizes not only your ROI on the security tools, but also network performance and security profile.
Traffic forwarding leverages Flow Mapping® to deliver packets at line rate with negligible latency. Flexible traffic guiding means that tools only inspect the traffic that is most relevant, and don’t waste cycles on traffic that doesn’t require inspection (or can’t be inspected by a particular tool). Tool health monitoring and bypass protection prevents congested tools from impacting network performance. Sharing the traffic load across multiple tools not only improves throughput, but also provides resiliency in the event of a tool failure. Updating, adding, or replacing inline tools no longer impacts network uptime.
A good security profile that keeps your data safe requires an infrastructure that takes cybersecurity tools into consideration. GRIP integrates with your dual-path network architecture so that you don’t have to compromise security for network resiliency or vice versa.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today