Flesh and Code: Advanced Threat Detection, Served Two Ways
Nation state. Breach. Data Loss. Some might say that today’s computer threats are becoming increasingly intricate and complex. Some, but not me. The threats are the same, the targets are the same. The vulnerabilities are the same. Some of these teams are better than others. Some have more resources than others. Some just have more time to sit and wait it out until the moment presents itself. Patience is the most sophisticated weapon there is in these cyber wars. Patience is the weapon, patience is the method. Patience, dear reader, is advanced.
In the following paragraphs we’re going to slice this topic up in two ways. First, we’re going to talk about Advanced Threat Actor Detection — detecting nation state, cybercrime and other organized threat actors. Then we’ll discuss Advanced Threat Detection — what’s required to create a top-tier advanced detection strategy. The former discusses the adversary, the latter discusses the level at which you’re playing when it comes your own advanced persistent threat detection strategies. Flesh and code.
The Flesh
What is an Advanced Persistent Threat (APT)? Besides being an acronym that launched a thousand startups? I’ll cut to the chase and tell you what they’re not. They’re not cyborgs, they’re not some kid wearing a hoodie in his mom’s basement and, most importantly, they are not a thing you can prevent, and anyone who tells you they can is lying to you. APTs aren’t vampires. They come in whether you invite them or not. Spoiler alert: You’re already inviting them by your lack of advanced-threat detection chops, but we’ll get to that in a second. Once they’ve come in and started raiding your fridge, how do you get them out? What’s more, when they’re just taking one egg at a time, how long until you realize you can’t make any more omelets?
Who Are They?
Hubris and the hound.
I have a 10-year old Beagle named Kona. She’s probably closer to 12, but I’m in denial so leave me alone. Kona is smarter than your average hound and loves nothing more than to find a nice, soft, expensive carpet and then pee on it.  I’ve gone to some extreme lengths to mitigate this attack up to and including never moving somewhere that doesn’t have all hardwood floors. Our last house fit that bill except for wall to wall carpet in the basement den. We also have cats that have better manners and I didn’t want to limit their mobility because my dog is a jerk. I had the bright idea to buy a dog gate at the top of steps that included its own cat door.
I’ve gone to some extreme lengths to mitigate this attack up to and including never moving somewhere that doesn’t have all hardwood floors. Our last house fit that bill except for wall to wall carpet in the basement den. We also have cats that have better manners and I didn’t want to limit their mobility because my dog is a jerk. I had the bright idea to buy a dog gate at the top of steps that included its own cat door.
Smugly, I installed the gate and then left for the day, confident in my apex predator king of the castle status of my household. What do you expect I found when I arrived home? An even more smug beagle, asleep on my clean clothes in the downstairs den, 30 feet away from where she’d done all manner of vile digestive things to the carpet.
Aghast I stood, wondering how the fat Houdini had pulled this off. Until, that is, she trotted back up the stairs and deftly moved through the cat door of my new, soon to be ashes, dog gate. The cherry on top was thinking I’d locked the cat door part of the gate after the first incident, but it didn’t fully latch. Guess who was back downstairs the next morning?
I had miscalculated the size, skill, brazenness and patience of my adversary. When I thought I had eradicated her from my environment with, as it turns out, a half measure, she came right back in at the first opportunity. My point here, besides admitting I’ve been bested by an animal that enjoys rolling in the scent of dead things in the yard, is that defending against advanced adversaries involves defenses across the whole spectrum of attacker options. I initially put “sophistication” there, but one of our Applied Threat Research leaders, Justin Warner, brought up an excellent point. It’s less about some magic level of sophistication and ninja ability, and more about all the options for attack paths that the adversary can take. Options that you, the defenders, have given them.
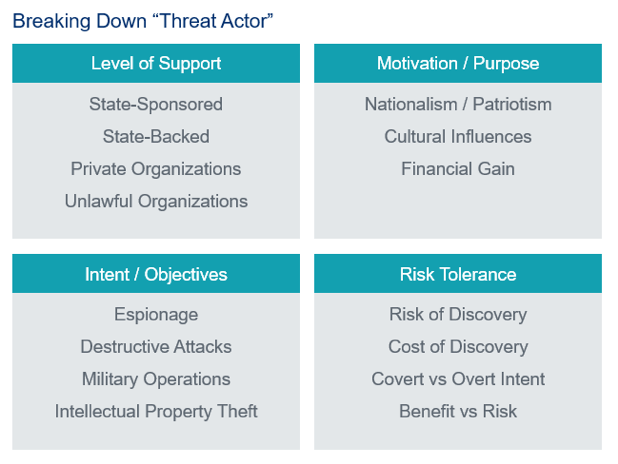
The conversation about stopping an advanced attacker must first begin with talking about who we’re defending against. First and foremost, we are humans defending against other humans. These are people with the same offices, bosses, deadlines and paychecks as you and I. And, like you and I, they make mistakes. The threats these humans encompass come in all shapes and sizes. Maturity, funding, experience, scale, motives and access are just a few of the many variables we must consider when discussing how to detect advanced threats. It also underscores the fact that if your adversary doesn’t come in one size, your defenses shouldn’t either.
For a deeper discussion on what these attackers and their organizations really look like, I invite you to check out my previous Gigamon blog, Money, Power and a 401k: Even Bad Guys Get Performance Reviews. I’ll admit that sounded 100 percent self-serving, but it’s only about 65 percent self-serving. I sustain myself on click-rates.
One of the foremost experts in the APT space is Jake Williams, Founder of Rendition Security, not to mention having up close and personal experience with the scariest threat actor groups known to man. Experiences that no matter how many drinks I buy him, he refuses to divulge. He’s also a friend of mine, and we got to talking about APTs. I asked him what his top points were that he’d want everyone to know about defending against advanced threats.
- On attacker tools: Sophisticated does not equal technical and technical does not equal sophisticated. Advanced attackers will use commodity and unsophisticated tools if they can get away with it. It is a mistake to judge the sophistication of the operation by the sophistication of the malware.
- On focusing the hunt: The “A” stands for “Advanced.” If you only find one C2 domain or one access method, that’s probably not it. “Single point of failure” is the opposite of advanced.
- On motivation: The “P” in APT stands for “persistent.” Make no mistake, they will be back. “Finishing” an incident is a myth, you only get them “out for now.” Everyone is a target. You are more valuable than you expect.
The Code
Advanced threats are not advanced threat actors. While they all pull from basically the same pool of research, advanced threats are just those that are ahead of your detection. How does actor-focused advanced threat detection differ from just the usual advanced threat detection? Do we also get swords? A moat? You’ll read other blogs that throw a bunch of fancy terms at you. They’ll tell you that you need X box that does Y thing to prevent Z scary thing.
Here’s the thing: Some of the most high-profile groups aren’t just using the latest and greatest in malware black magic. They also rely heavily on open source/off the shelf tooling. Tools like Cobalt Strike, Meterpreter and commodity RATs (Remote Access Tools) are being used by top-tier APTs such as Iran and Vietnam, as well threat actor groups like FIN7. For more information on FIN7 and their use of Cobalt Strike’s Malleable C2, see the blog post, Footprints of FIN7: Tracking Actor Patterns, written by our very own Justin Warner and Stephen Hinck. If you’re interested in reading more about how nation-states use the same tools as your own red teams, I’ve included a useful reading list at the end of this blog.
The truth about preventing advanced threats is that you can’t. Nobody can. They’re getting in. It’s your job to help stop the bleeding long enough to figure out what went wrong and how to fix it so you lose less blood next time. Because there will always be a next time.
Defense in depth didn’t start with information security, but we sure did appropriate it. Marketing materials have been beating that drum since the late 90s. Yet, 20+ years later, we’re no closer to getting it right today than we were back then. The term defense in depth originated as parlance for a military strategy that seeks to delay rather than prevent the advance of an attacker by yielding space to buy time. The phrase I want you to concentrate on is “delay rather than prevent.” Advanced attackers have more time, more money and more resources than you. They will get in.
It’s time to reevaluate what we mean by defense in depth. By reevaluate I mean we need to stop taking it so literally and assigning a hard number of things that check the box of “good enough.” It’s not just boxes like firewalls and IDS. It’s not just a software stack like antivirus and Suricata. There is no literal number. How much is too much? How much is not enough? You can drown in shallow water just as easily as you can sink in the ocean.
Okay, but seriously, what do I need to buy?
“If you spend more on coffee than on IT security, you will be hacked.
What’s more, you deserve to be hacked” ― Richard Clarke
When it comes to what you’re going to spend money on to fight advanced threats, it’s important to clarify one point. It’s generally unwise to spend money defending against something that’s almost entirely indefensible.
Solutions to complex problems are rarely, if ever, composed of just one big thing, single service, box or group of people. When I talk about a solution it’s best to visualize a large box full of various things that complement the other things in the box, if assembled correctly and specifically to your environment, but one missing thing doesn’t break all the other things. If the transmission in my car catches on fire, I’m not going anywhere. If the turn signal bulb burns out, I can still get to where I’m going although I’ve just made the journey a tad riskier.
If we want to even begin discussing a threat detection strategy that can be considered advanced, then we’re talking not just about attacker behavior, we need to talk about an entire spectrum of detection.
The Oxford dictionary defines “Spectrum” as being used to classify something in terms of its position on a scale between two extreme points. For our purposes, our points are “Can’t see a thing” and “Oh boy, look at all the things.” How do we get from fumbling blindly in the dark to seeing all the things in front of us? Let’s break that progression down into easily digestible bullet points.
- The proper combination of relevant (this matters to us as a company) and timely (this stuff isn’t five years old) indicator matching.
- Simple, behavioral detection and signature matching analytics.
- Complex behavioral detection. Multi-event matching and statistics.
Those three points are tools for a well-groomed detection team. Even then, that team needs to be fed with the right intel pipelines. On top of all of that, any rules you create from these methods need to be maintained. It’s not enough for Vendor X to claim they’ve got the market cornered on advanced threat detection, they need to show their work and demonstrate how or why their intel makes their detection better.
Release the ATR: Gigamon Applied Threat Research Team
Now that we’ve sufficiently covered the human element of these advanced attackers, it’s only fitting we close with a discussion on the human element of defense. Enter Gigamon Advanced Threat Research (ATR). ATR is our user zero. They are the first users ensuring that the product continues to grow in a direction that enables the analyst. ATR has three main goals to achieve that objective.
Goal 1: Utilize Public and Private Data to Produce Focused Internal Intelligence
I love Twitter. Not just love, I adore it. It’s been my personal go-to one-stop shop for everything security related since I first transitioned my career from printer repair jockey to the world of information security. One of the reasons it was, and remains, so critical to my own workflows is that inspiration can be hard to come by. All of our respective experience tanks are finite. Twitter has moved beyond just social media — it’s now an intelligence gathering tool. An important one at that.
After spending a few minutes (who are we kidding, hours) on Twitter, following your favorite red team-themed accounts and leads upon leads about offensive tradecraft at your fingertips, you will certainly come away with more than a handful of new tricks the bad guys are using. Then what? Therein, as the Bard would tell us, lies the rub.
Whose job is it to do more than read a tweet? Who will gather relevant context and track use of that technique? Sure, there are always those over-the-counter threat models being pedaled everywhere, but are they specific enough to actually be practical to your unique challenges and, what’s more, do they contain the needed context to answer the age-old question of “Why Should I Care?” Who has the time to take all that Twitter magic and turn it into something that matters? Your ATR team, that’s who.
ATR utilizes its intelligence function to track emerging threat behavior. They constantly hunt and discover tactics and techniques being used by a range of threats. Examples of these discoveries can be seen in their work on Google Chrome Extension malware or discovery of zero-days vulnerabilities in Adobe Flash getting exploited. They also analyze existing and new techniques to proactively identify areas of interest for detection based on generic adversary models. At the end of the day, their output is not output for outputs sake. It is well researched, rich, technical intelligence to feed the detection beast.
Goal 2: Leverage Intelligence to Engineer and Maintain Detection Logic
With knowledge of the technique and context of use, the natural next step is to focus on detection. That’s where the ATR detection engineers come into play. Day in and day out, they consume internal tips and intelligence, emulate the adversary behavior to better understand it, and build detection capabilities. It’s important here to note that they aren’t just cranking out endless low-quality signatures and dropping them on your door step; they have their own tested and refined process using a range of methods at their disposal to build and publish detections in the product.
When we say build and publish detections, we don’t mean just with every new release of our Insight platform. ATR breaks the mold of traditional product cycles — they constantly research attacker techniques and push out those new detections as soon as they’re ready. The adversary doesn’t wait to attack; we don’t wait to defend. Better yet, they evaluate detections prior to release to ensure they are of proper quality and maintain those detections after release to downgrade confidence or modify logic when needed.
Goal 3: Prototype and Research Future Detection Capabilities
The final element of ATR, Research and Development, is possibly the easiest to understand at face value. Simply put, they are our dreamers. We’ve spent this whole article trying to humanize our adversary. ATR is our human response. You can’t catch all the bad guys without any good guys actively hunting threats and, most importantly, iteratively improving detection capabilities. ATR are those actual humans thinking about the future of the product. They are constantly and consistently refining its capabilities in order to discover and respond to threats we’re already seeing today and those that will inevitably follow tomorrow.
In Conclusion
The bottom line is that computers are hard. Much like me standing in the delivery room like a dummy when my wife was delivering our child, they look pretty but aren’t very helpful. At least, not at defending themselves from threats that are both constantly evolving to take advantage of new vulnerabilities or still firing and hitting things still unpatched from long ago. Regardless of whether we’re talking about threats that are advanced or advanced methods of detecting threats, you must train as you fight, with both flesh and code.
Additional Resources
- “Insights into Iranian Cyber Espionage: APT33 Targets Aerospace and Energy Sectors and Has Ties to Destructive Malware.” FireEye.com. September 20, 2017.
- “Operation Wilted Tulip — Exposing a Cyber Espionage Apparatus.” Clearskysec.com. July 25, 2017.
- “Cyber Espionage Is Alive and Well: APT32 and the Threat to Global Corporations.” FireEye.com. May 14, 2017.
- “Alert (AA18-284A): Publicly Available Tools Seen in Cyber Incidents Worldwide.” United States Department of Homeland Security. October 11, 2018.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group. Share your thoughts today.
Share your thoughts today