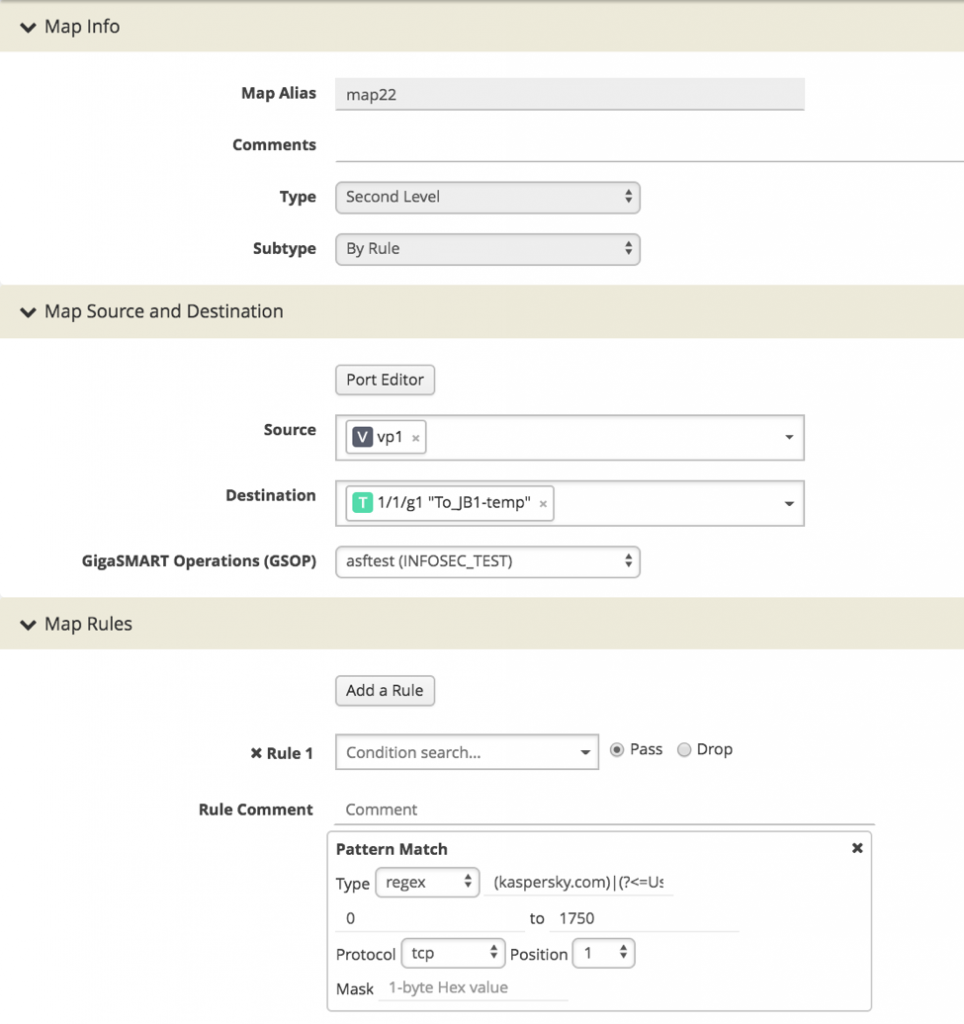
Finding Kaspersky Traffic with GigaSMART Application Session Filtering
With Gigamon GigaSMART® Application Session Filtering (ASF), we can leverage patterns in raw network traffic to detect machines communicating with Kaspersky. To do this, we’ll create a maprule that matches some regex we’ve discovered by analyzing packet captures (PCAPs) of machines talking with Kaspersky. We’ll take all the packets that match this pattern and then route them out of a tool port to a machine running tcpdump.
During our analysis, we found a few patterns we can use. The obvious one is anything calling to *.kaspersky.com. However, we also identified what appears to be a machine generated User-Agent that starts with an @.
Examples:
- dnl-03.geo.kaspersky.com
- User-Agent: @hEKzPRNa0lItsGIjysY
The regex we’ve used to test this is:
| (kaspersky.com)|(?<=User-Agent:)\s*@\w* |
Figure 1 shows how this appears in the maprule.
Once we’ve detected Kaspersky, it will start flowing to our tool port. The result is Kaspersky packets and more importantly, the IPs that are talking to Kaspersky appearing in our tcpdump.

Figure 2: traffic to Kaspersky IPs fetching updates after matching our ASF rule and hitting our tool port.
From here, we now just hunt down the sources and remediate them.
To learn more, don’t miss our webinar “SOC Talk: Phantom Automation for Faster Response Time.” We will walk you through how to use the GigaSECURE Security Delivery Platform to determine if, for example, Kaspersky has been removed and show how the Phantom Platform can automate the identification and removal process.