WannaCry: What We Know So Far . . .
An unprecedented cyber-attack by a ransomware variant known as WannaCry—which encrypts a computer’s files and demands payment to unlock them—has propagated at a speed never before seen by cybersecurity researchers. To date, more than 75,000 systems across 100+ countries have been reported infected, with a major toll taken on operational services at targets such as Telefonica in Spain, the National Health Service (NHS) in the UK, and FedEx in the US (with European countries, including Russia, among the worst hit).
 Though the spread seems to be slowing, by no means has it stopped. Based on data provided by MalwareTec, The New York Times has compiled an animated map showing just how fast WannaCry has disseminated, and it’s certainly an eye opener to those who regard cybersecurity as a nuisance problem rather than a potential enterprise-level risk.
Though the spread seems to be slowing, by no means has it stopped. Based on data provided by MalwareTec, The New York Times has compiled an animated map showing just how fast WannaCry has disseminated, and it’s certainly an eye opener to those who regard cybersecurity as a nuisance problem rather than a potential enterprise-level risk.
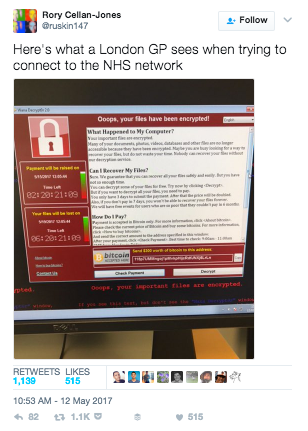
One of the first organizations to report the attack was the NHS in the UK, where security teams continue to work around the clock to restore the systems of some 45 affected hospitals in England and Scotland. Incredibly dangerous, the attack put patient safety at risk as it left some hospitals and doctors unable to access patient data and led to the cancellation of operations and medical appointments.
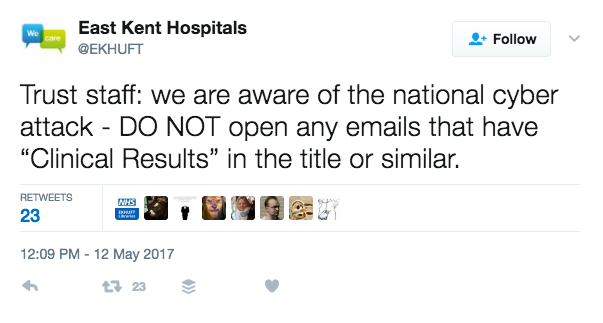 The Twitter account for NHS’s East Kent Hospitals sent a message to all staff indicating that the ransomware may have been attached to an email with “Clinical Results” in the subject. If this report is true, it appears that hospitals were specifically targeted.
The Twitter account for NHS’s East Kent Hospitals sent a message to all staff indicating that the ransomware may have been attached to an email with “Clinical Results” in the subject. If this report is true, it appears that hospitals were specifically targeted.
While it’s likely that the NHS received the majority of the early press on Friday due to the time of day the attack took hold (early morning in the UK), WannaCry spread fast and not only to other organizations around the world, but also to devices and systems other than standard employee workstations. German rail operator Deutsche Bahn, for example, said that while the attack did not disrupt train services, it did infect its systems, including station display monitors.

A display at Chemnitz station in eastern Germany shows a ransom demand on Friday night. Photograph: P. Goetzelt/AFP/Getty Images
How does WannaCry work and why is this attack unique?
While this ransomware variant is actually rather run-of-the-mill, the way it is infecting systems and spreading so quickly is unique. Most ransomware relies on a user to click a malicious link or file attachment in a phishing email to infect a computer. While cybercriminals can spam out thousands or even millions of phishing emails a day, a successful infection still relies on an unwitting end user to become an unwilling accomplice and trigger the attack. While this is still an incredibly effective technique, it limits the overall ability for most ransomware to spread as each individual target user needs to fall for the trick. Not so with WannaCry.
It appears that once a single instance of WannaCry infects a PC behind the firewall, it can move laterally within networks and self-propagate to other systems. Initial analysis by security researchers indicates that it can do this by: scanning and identifying systems with ports 139 and 445 open, listening to inbound connections, and heavily scanning over TCP port 445 (Server Message Block/SMB), which allows the malware to spread on its own in a manner similar to a worm. The worm then loops through every RDP session on a system to execute the ransomware as that user targeting admin accounts. It also installs the DOUBLEPULSAR backdoor and corrupts shadow volumes to make recovery more difficult.
WannaCry is able to do this where the PC is open to listening and has not been updated with the critical MS-17-010 security patch from Microsoft that was issued on the 14th of March and addresses vulnerabilities in SMBv1 (Microsoft doesn’t mention SMBv2). Windows 10 machines were not subject to the vulnerability addressed by this patch and are, therefore, not at risk of the malware propagating via this vector.
Additionally, Talos has observed WannaCry exploiting DOUBLEPULSAR, a persistent backdoor that is generally used to access and execute code on previously compromised systems and that documented the offensive exploitation framework released as part of the Shadow Brokers cache.
What happens to infected systems?
Once the ransomware infects a system, it starts encrypting everything it can find. The file taskche.exe searches for both internal and external drives mapped to a letter such as “c:/” or “d:/” so that mapped network shares could also be affected. When it finds files of interest, it encrypts them using 2048-bit RSA encryption. How strong is that? Well . . . a DigiCert post calculated that it would take 1.5 million years with a current and standard desktop machine to crack it.
The user then receives a notification on their screen demanding $300 in Bitcoin to release files and restore the system. Otherwise, if the ransom is not paid, the files will be rendered permanently inaccessible or out-and-out deleted. Some reports indicate that if the user doesn’t pay within six hours, the ransom amount will increase to $600 while others indicate that the user has three days to pay. This is incredibly insidious social engineering as it creates a sense of urgency for the user to just pay the ransom or else face a rising cost or losing everything. A sense of hope is also instilled by providing the ability to decrypt a small selection of files, attempting to demonstrate to the user that if they comply with the extortion and pay the ransom, they will receive access to their remaining files.
It should be noted that the criminals behind the attacks are under no obligation whatsoever to provide decryption keys. So paying the ransom may not actually result in recovering access to the system and files. What’s more, paying a ransom not only marks the user as a potential target for future extortion attempts, but it also helps fund the very criminals that perpetrated the crime to develop new and more sophisticated attacks.
Why the spread is slowing down: the kill switch
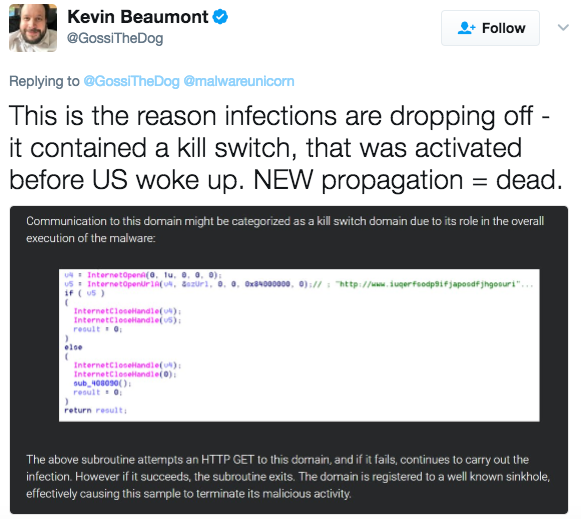
Talos noted early in the investigation of the attack that WannaCry was sending requests to the domain “iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com.” This is likely a human generated domain as the characters included largely consist of keys in the top row of the keyboard. These patterns are generally the result of someone “mashing” the keyboard and are easily recognizable by security researchers.
It appears that if WannaCry can communicate with this domain, it will stop execution and not infect the system. As this domain was not registered, each infection would attempt communication, fail to reach the domain, and, therefore continue to execute and infect the PC. Once the ransomware became able to communicate with that specific domain, it would stop with the domain, once registered, acting as a “kill switch.” This is highly unusual and appears to have been hardcoded into the malware by the creator in case he, she, or they wanted to stop the spread of the attack.
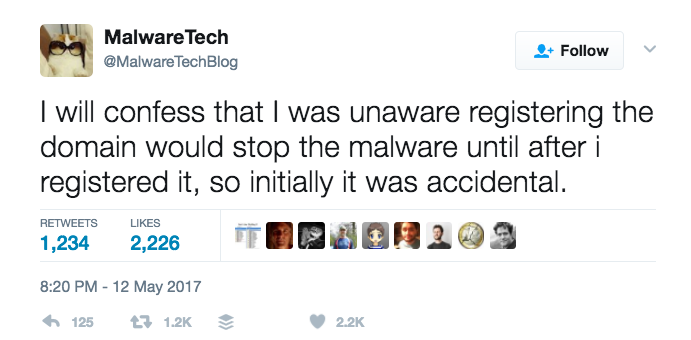
 A wily security researcher @malwaretechblog, with the help of Darien Huss from security firm Proofpoint, found and activated the kill switch by simply registering the domain.
A wily security researcher @malwaretechblog, with the help of Darien Huss from security firm Proofpoint, found and activated the kill switch by simply registering the domain.
“I saw it wasn’t registered and thought, ‘I think I’ll have that’,” said MalwareTech. The purchase cost him $10.69. Immediately, the domain name was registering thousands of connections every second.
While it seems almost anti-climactic, the kill switch appears to have worked and is slowing the spread of infections. Unfortunately, we can likely expect that copycats are already working on variations of the attack and with bad guys everywhere learning a great deal from this incident, we can also expect new variants and modifications to the attack to launch soon.
 When the Conficker worm was running rampant and creating a huge botnet back in 2008, , a security researcher similarly found that it was calling home to randomly generated domain names for Command and Control instructions. He was able to limit Conficker’s ability to execute any commands by registering all the domain names. Variant A and B of Conficker downloaded daily from any of 250 pseudorandom domains. While registering 250 domains a day was getting a little expensive and time consuming, it was still possible for defenders, collectively know as the Conficker Cabal, to keep ahead of the attacker. This strategy fell apart when the attacker released Variant C, which downloaded daily from 500 of 50,000 pseudorandom domains. We can likely expect that future variants of WannaCry and copycats will employ a similar approach and ensure that discovering and activating a simple kill switch will not be effective ever again.
When the Conficker worm was running rampant and creating a huge botnet back in 2008, , a security researcher similarly found that it was calling home to randomly generated domain names for Command and Control instructions. He was able to limit Conficker’s ability to execute any commands by registering all the domain names. Variant A and B of Conficker downloaded daily from any of 250 pseudorandom domains. While registering 250 domains a day was getting a little expensive and time consuming, it was still possible for defenders, collectively know as the Conficker Cabal, to keep ahead of the attacker. This strategy fell apart when the attacker released Variant C, which downloaded daily from 500 of 50,000 pseudorandom domains. We can likely expect that future variants of WannaCry and copycats will employ a similar approach and ensure that discovering and activating a simple kill switch will not be effective ever again.
So now what?
Mitigation Recommendations
- Ensure all pre-Windows 10 PCs are fully patched. Patch the Windows 10 ones just to be safe, too!
- Ensure Microsoft bulletin MS17-010 has been applied.
- SMB publically accessible Internet ports 139, 445 should be immediately blocked to prevent inbound traffic.
- Block all known TOR exit node IP addresses at the firewall. These are generally available from security intelligence feeds.
- If for some reason you can’t patch a device (medical device or other closed architecture systems), make sure to disable SMBv1.
Prevention Recommendations
- Ensure you are running the most up-to-date operating system on all your devices, not just PCs.
- Have a formal patch management system in place to ensure that all vendor patches are applied to all endpoints in a timely manner.
- Install some form of endpoint protection for anti-malware on all your systems and ensure you apply regular updates.
- Simply having updated firewalls and endpoint protection is no longer enough. This attack moved laterally behind the firewall. This means that end-to-end, complete network visibility and security tools that can detect, prevent, and mitigate threats throughout your physical, virtual, and cloud networks are now mandatory.
- Ensure not only that you have business continuity and disaster recovery plans in place, but that they are updated and tested regularly.
- Backup everything! And ensure that you have offline backups as attackers also frequently target backup systems to increase the odds that you will pay the ransom.
- Train your users! Employees should receive both security awareness training to help them identify and report threats and protect themselves as well as traditional security training to help them know what is expected of them and how to comply to organizational security policies and procedures.
Related Technical Resources
- https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
- https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
- https://gist.github.com/rain-1/989428fa5504f378b993ee6efbc0b168
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today








