Networking Field Day #15: Enhanced Visibility into SSL/TLS Traffic
 Last week, Gigamon hosted Networking Tech Field Day #15, where we welcomed network technology experts from a variety of companies to learn more about the latest enhancements to our GigaSECURE Security Delivery Platform, featuring our new inline SSL decryption functionality.
Last week, Gigamon hosted Networking Tech Field Day #15, where we welcomed network technology experts from a variety of companies to learn more about the latest enhancements to our GigaSECURE Security Delivery Platform, featuring our new inline SSL decryption functionality.
Kicking off the event, our VP of Products Ananda Rajagopal gave a high-level overview of GigaSECURE and the criticality of visibility before passing the baton to me and Technical Marketing Engineer Anish Sharma to deliver a deeper dive and demo of the platform’s SSL/TLS decryption capabilities.
Before moving on from my first “stats” slide, delegates had already joined the conversation.
While heads nodded through the first three stats, they took a tilt at the last. “Only 33% using encryption?” one delegate said. “I’m surprised. Those malware guys need to up their game. I’d expect 80-90%.”
My team had to agree. But while that number is low now, we ventured to guess it might quickly rise if we see a large enough attack on SSL. The question is: Will companies wait for that to happen before investing in the necessary security?
Traditional (yet not ideal) approaches to decrypting/inspecting SSL traffic for malware or Web vulnerabilities have included:
- Web proxies or firewalls. If you turn on decryption, not only does CPU go through the roof, but you also can’t distribute traffic to multiple tools.
- Load balancers. It’s an all-or-nothing solution. Not only is it difficult to distribute traffic in a Layer 3 device (e.g., it requires complex routing from load balancers to security tools), but there’s limited traffic selection and weak inline bypass.
- Dedicated SSL decryptors. Again, these offer limited traffic selection, as well as limited interfaces, which can create appliance sprawl as many of these tools will need to handle your decryption needs.
Decryption is a heavy operation, and that’s why GigaSECURE’s ability to “decrypt once and feed to multiple tools” is so compelling. It offers both inline and out-of-band decryption on any port of application—with supported ciphers now including Diffie-Hellman (DH), Diffie-Hellman Ephemeral (DHE), Perfect Forward Secrecy (PFS) and Elliptic Curve—in addition to providing scalable interface support (1Gb – 100Gb); certificate validation and revocation lists to strengthen an organization’s security posture; and strong privacy compliance with URL categorization before decryption).
For more specifics, don’t miss the live demo given by Anish.
Responsible Man in the Middle
People hear man in the middle (MitM) and they automatically think malicious attack. However, not all MitM intercepts are made the same. And what Gigamon offers is “responsible,” “lawful/legal intercept,” or “sanctioned” MitM interception. At Tech Day, we used “Jack goes to Dropbox” as a simplistic example of how it works.
If Jack goes to Dropbox, Dropbox hands over a certificate saying, “I’m Dropbox, signed by DigiCert.com.” Gigamon takes that same certificate, conducts checks to ensure it’s good, and re-signs it using our own Gigamon certificate authority (CA). We aren’t reducing the trust levels in any way; we’re simply in the middle.
 Not surprisingly, the delegates raised some important “what if” and “how about” questions—maybe some of the same ones you’re asking yourself right now. They know their stuff! And it was great to hear how they appreciated our MitM “straight talk.” To not miss any details, I’d, again, suggest tuning in to the session recording, which also includes a live MitM demo.
Not surprisingly, the delegates raised some important “what if” and “how about” questions—maybe some of the same ones you’re asking yourself right now. They know their stuff! And it was great to hear how they appreciated our MitM “straight talk.” To not miss any details, I’d, again, suggest tuning in to the session recording, which also includes a live MitM demo.
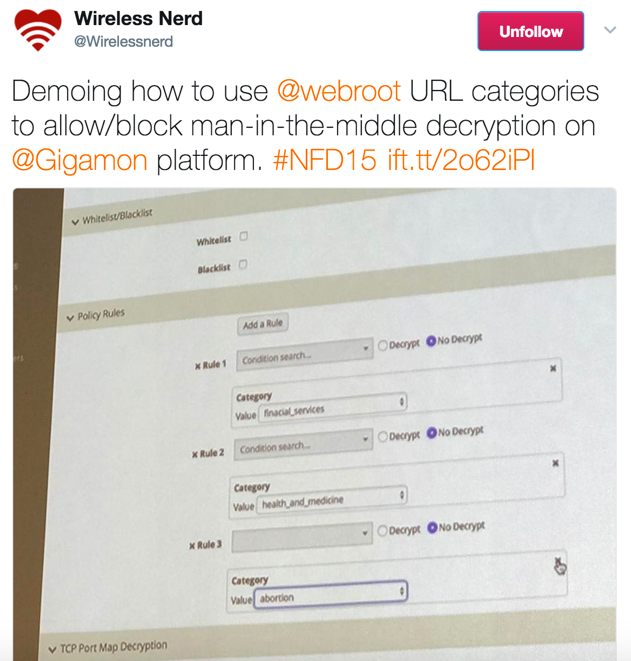
URL Categorization
The GigaSECURE URL categorization feature addresses the concerns of employee privacy when choosing to decrypt SSL. For example, let’s say employees Jack and Sally are browsing different websites from their work network. Jack was seen uploading a file into his private Dropbox account. In this case, it could be argued that the employer has a right to inspect this traffic to ensure that Jack is not uploading any sensitive information to his personal account. Sally, on the other hand, went to her bank account to check her balance and also logged into her healthcare provider to check on some test results. While done on a work network, this constitutes personal employee information, which her employer should not decrypt.
To differentiate traffic types, Gigamon uses a URL categorization service provided by Webroot. With this capability, a company can configure the categories it deems personal and bypass their decryption.
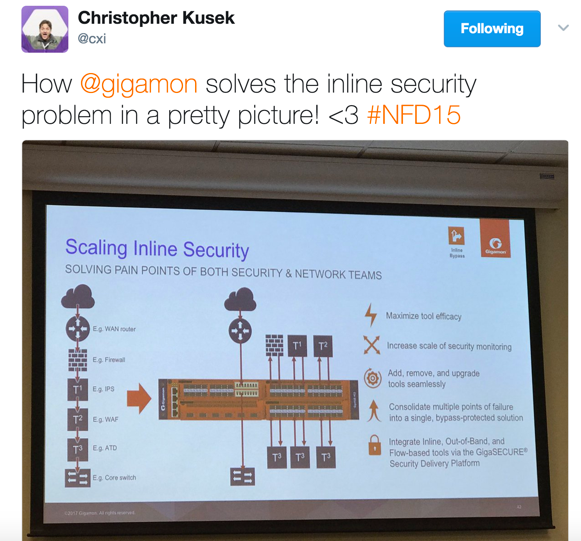
Inline and Out-of-Band Tools
Imagine if you want to isolate and send: email traffic to an email security tool like Proofpoint; Web traffic to a Web security tool like Imperva; or all attachments to a DLP solution and then aggregate and send all of this traffic, serially, to a Palo Alto Networks and FireEye tool before passing it out to the internal network. Then imagine that, in the case any of these tools should fail, traffic will continue seamlessly. This is what our inline bypass solutions help do.
With SSL decryption happening in the network, it is extremely important to preserve current support for inline and out-of-band tools. Thus, after traffic decryption, we can send the decrypted traffic through a serial arrangement of a Palo Alto and FireEye tool so that both tools can inspect the traffic and deem it safe before it is re-encrypted and re-injected into the network.
Similarly, you can also decrypt and load balance traffic across a sequence of IPS devices for malware inspection prior to re-encrypting and passing it back into the network. Or you can also take SSL traffic from different networks and pass it through a common set of security tools, all of which is facilitated by GigaSECURE’s inline arrangements.
RSA NetWitness
RSA Senior Engineer Jim Hollar also joined us to present on RSA NetWitness. As he said, RSA NetWitness may be in a category called SIEMs—but not all SIEMs are created equal. RSA NetWitness is into security analytics and can fully capture the completed conversation in the network. And RSA NetWitness is a unique product that captures all the traffic in a network and offers a comprehensive investigation of it as well as from the endpoint.
 So how does Gigamon come into the picture? Well, a SIEM is only as good as the data it can ingest from the network. For a long time, most security tools were blind to encrypted traffic, missing critical portions of network traffic. With Gigamon’s SSL decryption feeding unencrypted traffic to the tools, RSA NetWitness can spot a whole host of malicious activities that were lurking inside encrypted communications.
So how does Gigamon come into the picture? Well, a SIEM is only as good as the data it can ingest from the network. For a long time, most security tools were blind to encrypted traffic, missing critical portions of network traffic. With Gigamon’s SSL decryption feeding unencrypted traffic to the tools, RSA NetWitness can spot a whole host of malicious activities that were lurking inside encrypted communications.
All in all, Tech Day was a great validation of Gigamon’s approach to SSL decryption. We are focused on helping our ecosystem partners succeed, removing the burden of encryption and decryption from security tools so they can focus on what they do best—which is looking for malicious behavior. By moving a critical, but highly process-intensive operation like SSL decryption from security tools to our platform, Gigamon continues to deliver on its mission to be the security delivery platform of choice for connecting all security tools.
Stay tuned for more blogs on our Security Delivery Platform as well as our upcoming Cloud Field Day (July 27-28) and Network Field Day (September 13-15).