Visibility into Akamai and AmazonAWS Traffic
Although the rise in the adoption of content delivery networks (CDNs) such as Akamai and AmazonAWS has improved the speed of online services, it has caused a new problem: Traffic Visibility.
Traditional NetFlow exports will tell you where the traffic on your internal network is headed on the Internet, but not the specific Internet site. This is because most of the major Internet sites we visit today are hosting content on CDNs. I estimate that 95% of the companies collecting flows today are only getting the source and destination IP address of a flow. This means that one of the IP addresses will belong to the company and the second IP address will belong to the hosting provider of the Internet site the traffic is headed for. In other words, we can’t discern from traditional NetFlow the actual website being visited.
Below is a typical Cisco NetFlow report showing the top destinations.
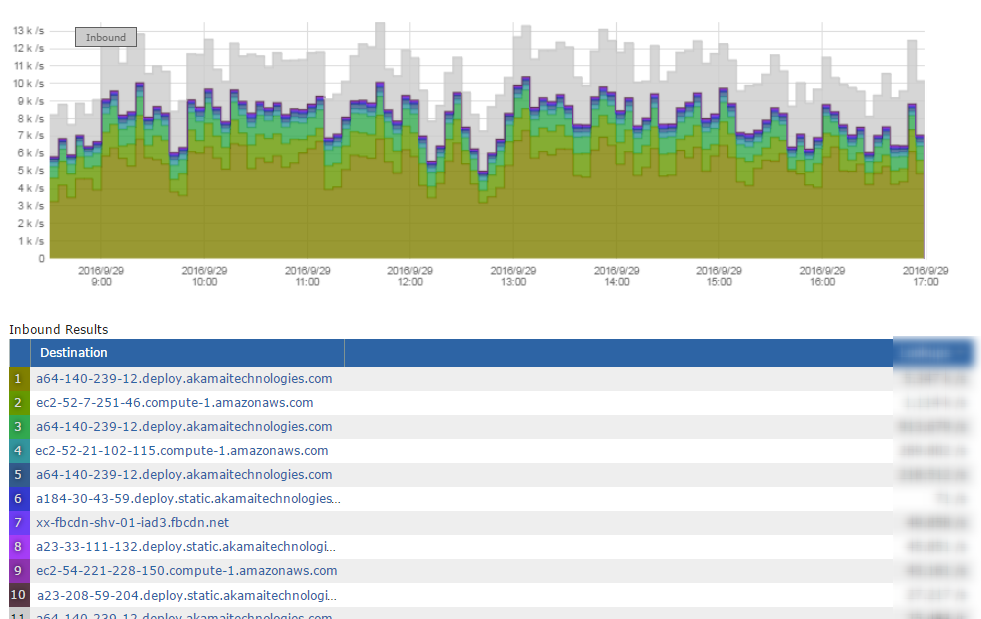
Cisco NetFlow before Gigamon
Notice that most of the traffic is going to either AkamaiTechnologies or AmazonAWS. Although this is certainly more helpful than what Simple Network Management Protocol (SNMP) would offer, we still don’t know where this user’s traffic is going beyond the CDN. To add to the confusion, a single CDN IP address could be hosting content for thousands of Internet sites or Fully Qualified Domain Names (FQDNs).
Gigamon appliances perform deep packet inspection on every packet they receive and export the data streams in IPFIX with rich metadata that can include details such as the FQDN. Plixer’s Gigamon Integration leverages this metadata from Gigamon and inserts it into the reports when viewing data on other flow exporters. See below:
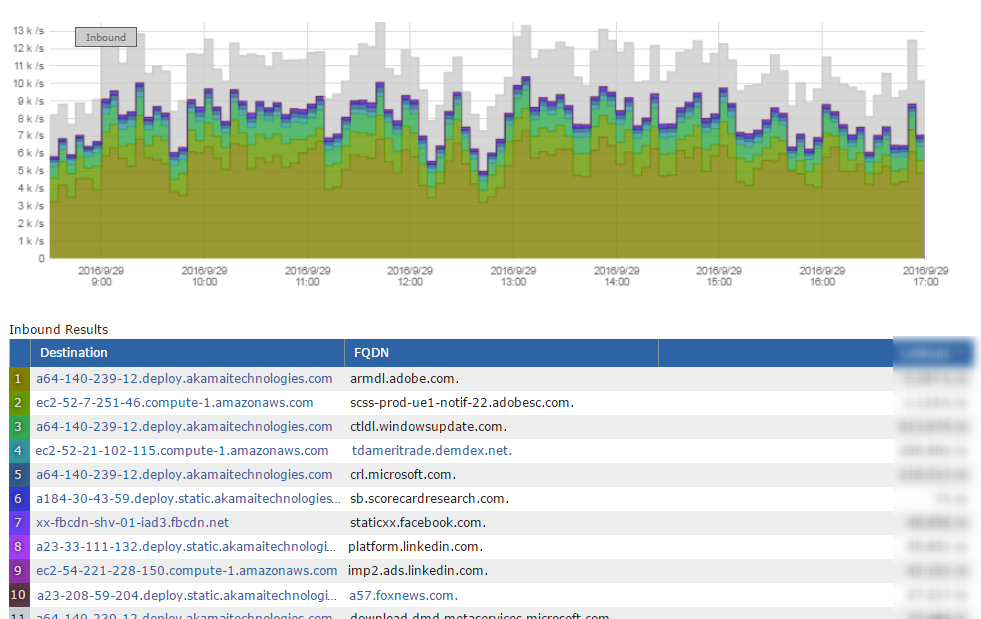
Cisco NetFlow after Gigamon
Notice the new FQDN column, which provides the insight we need when investigating a security issue or an application performance problem. As you can see, knowing the FQDN not only provides insight into the application in use, but also overcomes a second emerging problem with NetFlow. More and more Internet traffic is traveling on port 443—which generally means the communication is encrypted.
Sites like LinkedIn, Facebook, Google, Twitter, Salesforce, and more have all switched to HTTPS. In fact, since 2014, the volume of HTTPS traffic headed for the Internet has grown from about 3.8% to well over 70% today. The primary reason for the growth is the push from Google, who stated that they will prefer HTTPS websites when serving up search results. Using Gigamon’s extended metadata gives you considerable insight into the traffic even if you can’t decrypt it.
Whether the traffic is headed to a CDN, is encrypted, or both, Gigamon serves up traffic visibility where you need it most. Contact Gigamon today to start your evaluation.








