Visibility Is the Best Disinfectant for Ransomware
In case you haven’t read the headlines in the past nine months, ransomware is big business for cybercriminals. It turns out that holding files hostage is more profitable than stealing personal information and, like any other business-minded group, these criminals are investing in this new growth market. Some groups are even packaging ransomware kits and operating on a franchise model!
Even more ominous for enterprises is a September 15 public service announcement from the FBI warning that cybercriminals are getting more sophisticated:
“Recent variants have targeted and compromised vulnerable business servers (rather than individual users) to identify and target hosts, thereby multiplying the number of potential infected servers and devices on a network.”
That’s bad news for companies because it means that criminals are increasingly looking to hold your entire business hostage and not just the files on one person’s laptop. So, even more targeted ransomware attacks are coming … are you ready?
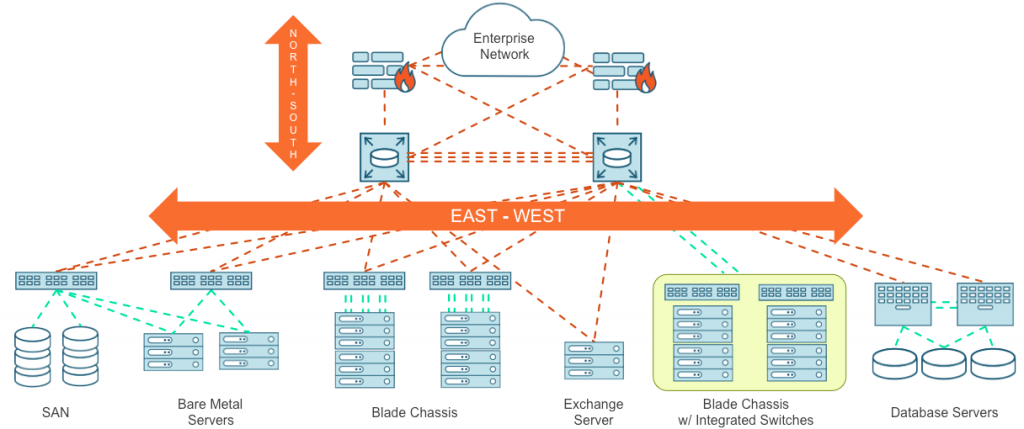
East-West Traffic Visibility Is the Gap in Your Defense
Unlike smash-and-grab attacks where the attackers are looking to break in and steal sensitive data before anyone notices, we can expect these more tailored ransomware attacks to take their time in order to encrypt the maximum number of files possible. These attacks will act much like advanced persistent threats (APTs), quietly surveilling your network, identifying targets, and establishing persistence before activating their malware.
If all you have in your security toolkit are solutions to prevent the initial infection, this should scare you because all it takes is one new variant to make it past your perimeter defenses.
To protect your business operations, you need to add east-west visibility to your security toolkit. While your perimeter defenses that inspect north-south traffic—traffic entering and leaving the corporate network—are still important, that’s not the gap in security defenses today. What’s missing is the ability to inspect every communication between servers inside the perimeter.
Enterprise IT needs a little more healthy paranoia and should assume that the bad guys are already inside. To quote long-time Cisco CEO John Chambers: “There are two types of companies: those that have been hacked, and those who don’t know they have been hacked.”
Gigamon + ExtraHop = Perfect Combination for Total East-West Visibility
Together, Gigamon and ExtraHop offer a great solution for visibility into all east-west traffic. Gigamon can send a clean feed of east-west traffic to the ExtraHop appliance, which performs real-time stream processing and reassembly to extract L2-L7 metrics.
With this level of visibility, you can now detect ransomware activity in real time, immediately identifying when files are overwritten with encrypted versions instead of, as with traditional solutions, having to wait until a user calls to complain about the strange note on their screen. You can also orchestrate firewall and network access control actions—thanks to the ExtraHop platform’s REST API that lets you kick off automated responses such as blocking offending IPs and revoking network access from infected systems. And you can even recover unencrypted files without backup. For example, in situations where you don’t have an up-to-date backup, you can recover files from the packets comprising the storage READ operation performed by the ransomware just before encrypting your files.
Read the ExtraHop whitepaper: Detect and Stop Ransomware with a New Mitigation Approach
All pretty cool, no? But the real kicker is that the Gigamon-ExtraHop solution offers much more than ransomware mitigation. The same deployment also lets you see all types of behavior contained in east-west communications, including privileged account activity, port scanning, banned protocol usage, weak encryption and deprecated cipher suites in use on your network, unencrypted traffic, traffic moving between test and production networks, and more.
Learn more about the benefits of the “perfect combo” from checking out this video.