Gigamon and Splunk: Using Metadata to Improve Security Visibility
Gigamon is looking forward to an exciting week at Splunk’s developers conference, .conf16: The 7th Annual Splunk Conference. For us, it’s all about the power of metadata to achieve actionable visibility so organizations can get better performance and intelligence from their security solutions.
Establishing reliable baselines and context for network activity is a daunting task. There are simply too many data sources belonging to too many different tools and solutions: endpoints, routers, switches, application servers (like DNS and Active Directory), existing security systems (like firewalls and intrusion prevention systems), and the list goes on. Even if it were possible to gather all the necessary data, there is simply too much of it to store and analyze easily. To make matters worse, turning on log-in systems, like firewalls and application servers, is computationally intensive.
How can organizations get access to the data that is so critical to proactive monitoring, detection and response efforts? And once they get it, how can they reduce the immense data volumes? To avoid overwhelming the monitoring infrastructure, the answer lies in retrieving a summary of relevant data using metadata elements found in Splunk® Enterprise with GigaSECURE Metadata Engine.
Sitting inside the GigaSECURE Security Delivery Platform is a full-blown Metadata Engine that provides useful security information about applications, devices, and users’ behaviors for each and every security tool connected to it. To solve the data deluge problem (which will only be exacerbated when speeds increase to 100G), organizations can simply turn on this function, feed the metadata into Splunk Enterprise, and gain greater understanding using the following capabilities.
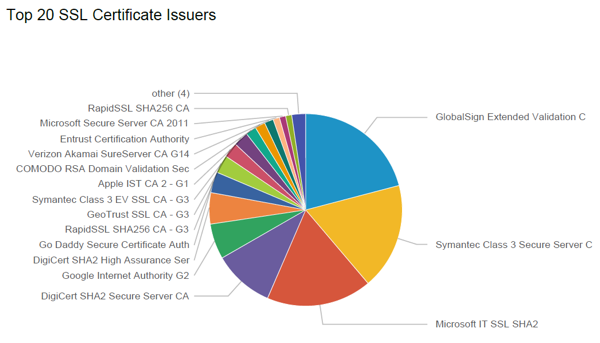
Using the Gigamon Metadata Engine, organizations have deeper SSL visibility. They can analyze all SSL certificates used in the organization, identify the issuing certificate authority and Web servers, and see additional details including expired certificates, self-signed certificates, and more. They can also detect suspicious certificates, their related servers tied to malicious sites, and which endpoints have visited those sites.
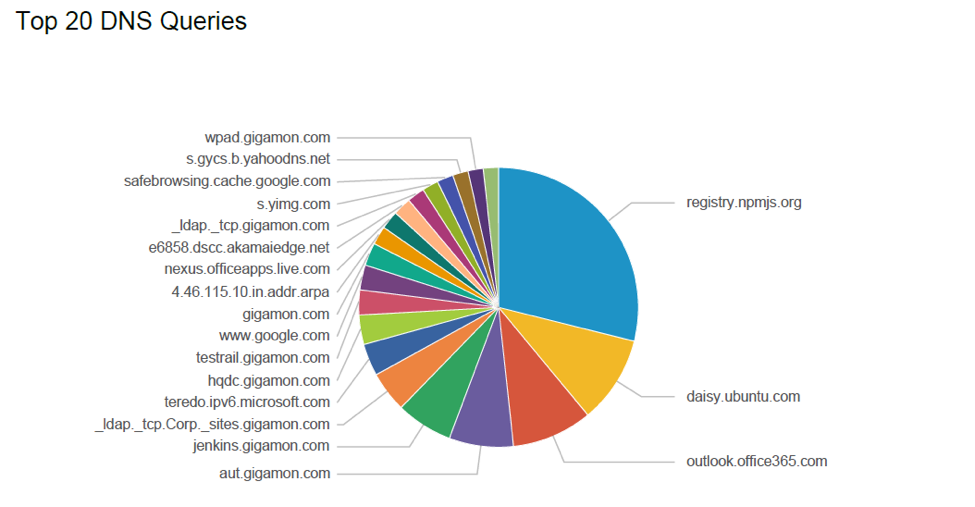
Organizations can also conduct DNS queries to see if an impacted device gained access to command and control functions. With the Metadata Engine, they can see the top DNS queries and responses as well as gain visibility to less common accessed DNS domain names and cross reference their reputation. For example, they might find a set of hosts regularly beaconing to their command and control server at regular intervals. Using Splunk Enterprise’s scripting language, they can programmatically search for such hosts at scheduled intervals and find compromised endpoints for further investigation and analysis.
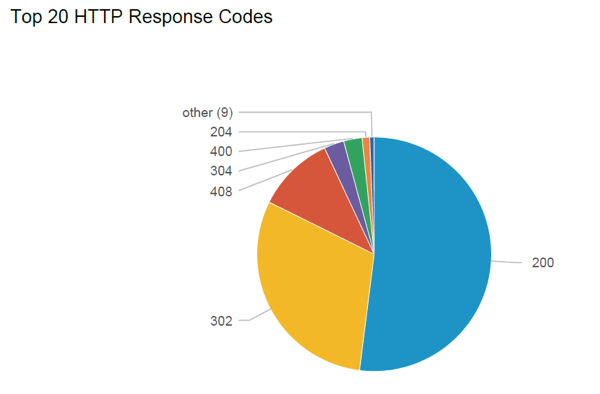
Another capability involves monitoring URLs and response codes. The Metadata Engine can parse out URLs from http streams and pass them to Splunk Enterprise. Analysts can perform a host of security checks starting with reputation analysis of URLs to see which webpages employees have visited whether for work related or personal use. They can determine which website breached their networks, gained access, and spread laterally.
Metadata analysis also detects irregularities by parsing response codes and looking for deviations from the normal (baseline) on a regular basis. An excessive increase in redirect codes such as the popular “302 redirect” may indicate a compromise of the organization’s servers, with the attacker directing traffic to an alternate server. A sudden increase in error codes such as “404 Page not found” may show a possible denial of service attack where the threat actor has caused the organization’s Web servers to be unreachable by browsers attempting to connect to them.
Many organizations already use Splunk software to centrally collect event and log data across their infrastructure. By integrating GigaSECURE Metadata Engine in combination with Splunk Enterprise, security organizations can leverage the rich metadata for improved threat analysis and intelligence.
Stop by our Gigamon booth # M12 at Splunk’s .conf2016 to learn more and read our recent white papers, Harnessing the Power of Metadata for Security and Nine Metadata Use Cases: How to Use Metadata to Make Data-Driven Decisions.