One Small Step for Visibility, one Giant Leap to the Public Cloud!
Public Clouds are here, so what is holding back enterprises?
A significant force in information technology today is the rapid evolution of the public cloud, especially Infrastructure-as-a-Service (IaaS). Attributes such as economies of scale, usage-based pricing, agility and elasticity are compelling enterprises to evaluate compute, network and storage infrastructure offered by a public cloud provider.
Unlike Software-as-a-Service (SaaS), where application ownership and security of information is the responsibility of the SaaS provider, an IaaS places the responsibility of application and information security on the tenant. (Of course, an IaaS provider is still responsible for the underlying infrastructure security.) In our conversations with customers, including many Fortune 500 enterprises, we have consistently heard that there are significant constraints holding back enterprises from running many mission-critical apps in the public cloud over an IaaS. The technical reasons behind these concerns often boil down to:
- Inability to access traffic, and by extension, information traversing the public cloud, for analysis
- Security concerns to run critical apps in view of the above
- Lack of sufficient tools in the public cloud. While a plethora of security analysis / IT monitoring tools exist for “on-prem” deployments, many of these tools do not have an equivalent in the public cloud
- Backhaul costs from the IaaS provider to an enterprise vary, should an enterprise choose to backhaul traffic from the public cloud infrastructure to the enterprise location where the tools are located
For example, in an on-prem deployment, there are options to get access to traffic from the infrastructure for real-time analysis—via TAPs (physical or virtual) or SPAN sessions (though TAPs are the favored method to gain reliable, non-intrusive access to mission-critical data in motion). When deploying applications in the public cloud, none of these options are available. In fact, even OpenStack has the same challenge, and is the reason why Gigamon introduced a tenant-based visibility solution last year and is currently collaborating with other industry stakeholders to champion “TAP-as-a-Service”.
Indeed, visibility to information traversing public clouds is critical for continuous monitoring and security of these application workloads.
Visibility to information traversing the public cloud—an industry first!
Today, we at Gigamon are excited to announce our plans to offer the industry’s first visibility solution for information traversing the public cloud. Customer trials of the solution for AWS EC2 begin today. Already, we have several partners and customers who have expressed deep interest in this solution and many have signed up to participate in the AWS trials.
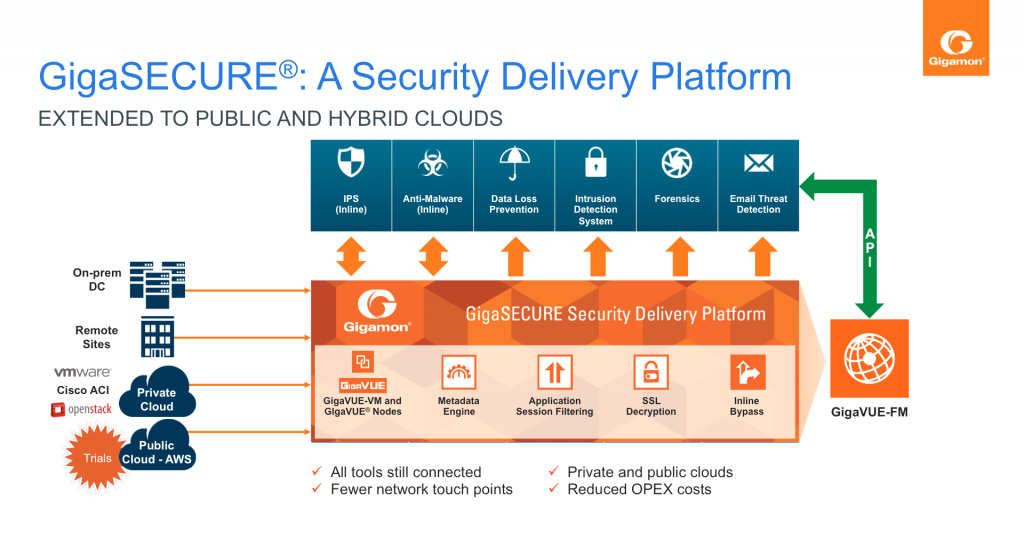
At Gigamon, we have always had a singular focus on visibility – the type of pervasive visibility that uncovers blind spots to help detect threats in the infrastructure. The formidable reach of our Visibility Fabric™, that underpins our Security Delivery Platform, becomes even more compelling when the pervasive reach that we already provide into Enterprises, Service Providers, Data Centers and Private Clouds is extended into the Public Cloud (see Figure below). With AWS as the dominant public cloud market leader, it was only prudent that we focus on AWS for our first public cloud solution. However, the design that is being implemented is extensible to other public cloud IaaS infrastructure.
This new solution would allow the customers’ security operations and network operations teams to centrally secure and monitor their on-prem and/or off-prem workloads, thereby providing comprehensive visibility regardless of workload location.
Solution flexibility
A key design criterion we have used in our solution is to provide maximum flexibility to the enterprise administrator to have different deployment options. These options would allow the enterprise administrator to choose where to perform the necessary analysis. The solution would therefore be applicable regardless of whether the tools are located in the cloud or on-prem:
- For some organizations, this means monitoring within the same AWS Virtual Private Cloud (VPC) instance as the workload.
- For others, this means having a dedicated VPC where the requisite tools are located and information from the VPC to be analyzed is sent to this dedicated VPC. IT organizations in regulated verticals or in verticals where the information is highly sensitive because of the associated intellectual property (e.g. high-tech firms), may find this option particularly appealing.
- Others may simply focus on a hybrid model, where the information is backhauled to the enterprise. This option is appealing for those enterprises that want to make better use of tools they have already invested on-prem and when backhaul costs are fixed (e.g. enterprises with a dedicated network connection to the public cloud provider such as AWS Direct Connect).
If you are interested in learning more or participating in the trials, visit http://www.gigamon.com/trials-aws or contact your Gigamon sales or channel representative.