The High Performance Security Delivery Platform
Updated October 28, 2021.
| The week of November 16th was a busy one. As I wrote in my previous blog, I was a part of SCinet security team at SC15 in Austin, TX and on Monday we finished 3 weeks of work to bring the network up and while my SCinet security coworkers used the monitoring tools to keep the network safe during the conference, I worked the Gigamon booth on the show floor and visited with current and future Gigamon customers who were either exhibitors or attendees at SC15. |  |
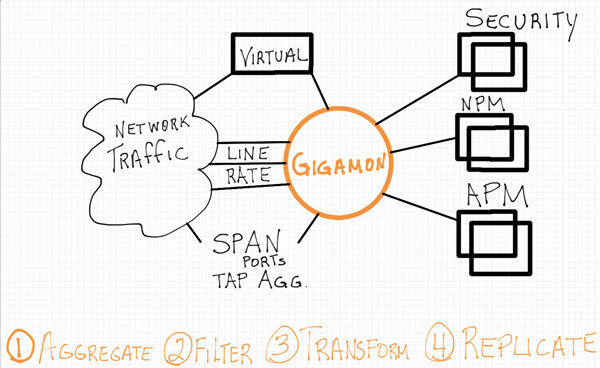
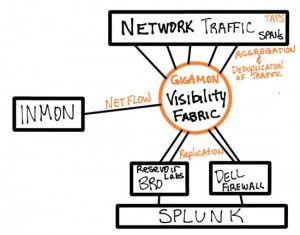
What is a Visibility Fabric?
During my time in the Gigamon SC15 booth, I was asked quite often what our product does? Some think we are a part of the network infrastructure, and many times we are when our inline solution is deployed, but we are not a Firewall, server load balancer, switch or router. Others think that we do data analytics, but we are not a malware detection, intrusion detection or prevention, SEIM, Data Loss Prevention, Application Performance Management or Network Performance Management tool. After I tell them that we don’t do any of these things, then they ask, well what do you do?
We provide a high speed, reliable, configurable pipeline to all of areas of your computing infrastructure where you desire to see the traffic flowing across your network. Think of it like being in a large room with multiple obstructions preventing you from seeing all areas of that room. If I stand in one part of the room I can clearly see what is going on around me, but I have limited visibility into the entire room due to obstructions or people standing in the way. I can observe and attest to what is going on in the area where I am currently located, I can even describe the safety and capacity of the area. But if I wish to see into other areas, I will need to setup some sort of video camera and a local monitor to provide me with additional visibility.
Most Security, Application and Performance management tools today thrive on access to the actual traffic that is flowing through your network. The more packets you get to these tools the better analysis they will provide. Gigamon is the means to get your tools the visibility they need.
Visibility is Key to Security
Being able to see the traffic traveling across your network is key to detecting malicious activity. Maybe you don’t need to see all parts of your network, so just setup monitoring for those areas of your network where the interesting traffic is traveling across. Most security and network managers would agree that the links to the Internet should be monitored and the second most common area is your data center. A good way to determine where to setup your TAPs or SPANs is ask yourself where your traffic flows and secondly, where are my most valuable assets located. That is where you should be watching.
You can’t protect against what you can’t see. I may have some outstanding security tools, but unless they get a copy of network traffic from the key areas of my network, they won’t be able see if a malicious actor is trying to steal the valuable information.
The other major threat to visibility is encryption. While encryption is a very useful technology that protects our valuable data from prying eyes, anything that is used for good can also be used for ill. Hackers are increasingly using encryption methods to hide their activities within your network. Having the ability to decrypt encrypted traffic in your network is a valuable tool to consider adding to your security delivery platform.
Security Doesn’t Have to Affect Performance
The number one reason why many network and computing professionals resist adding security measures to their network is that they believe it will adversely affect their ability to get their job done or it will degrade the performance of the computing network and thus impacts their end users.
During a time of employment at a major computer manufacturer and software development company, I recall many times when a fellow employee in the company would decide that they wanted to check out the new version of our network management tool and since it was available as a free download to all employees, it would be downloaded and installed. Then during the initial configuration, the tool would discover the topolgy of the network, which would interrogate every router and switch asking for SNMP data and for the names and addresses of all routers or switches that router or switch knew of. This single action would bring the network down.
Each year one of the most powerful networks in the world, SCinet, is designed to be very fast and support high performance computing for one week out of the year. Ensuring that SCinet is used for its intended purposes and not compromised or used for illegitimate purposes is an essential task. The SCinet security team did an amazing job pulling together the best products and the best engineers to accomplish this goal without sacrificing performance. Looking forward to doing it again next year.