What Is Inline Bypass? Keep Traffic Flowing Fast by Any Means Necessary
There are two big network trends right now that are working a little bit at cross-purposes. The first is that networks are getting faster, with 100Gb ethernet becoming more common and terabit ethernet visible on the horizon. At the same time, though, networks are becoming more complex, with more switches, more nodes, and more security and management tools.
Lots of the security tools are deployed inline, meaning that network packets have to flow through them, get analyzed (and maybe altered or even blocked) and flow out. But imagine if you upgrade your network speeds while keeping your tried and true inline tools in place. The tools might not be able to keep up with the speed of the packets coming over the wire.
If the tools take too long to process the network traffic, or if they get overwhelmed by the sheer volume of packets, that can mean you don’t achieve the full speed potential of your network infrastructure — and you might even end up with lost packets or network outages.
Inline Bypass to the Rescue
A next-generation network packet broker (NGNPB), like the Gigamon Visibility and Analytics Fabric, offers a way around this problem that still lets you get all the benefits of inline tools via a feature called inline bypass. As the name implies, inline bypass lets you route network flows around inline tools as needed.
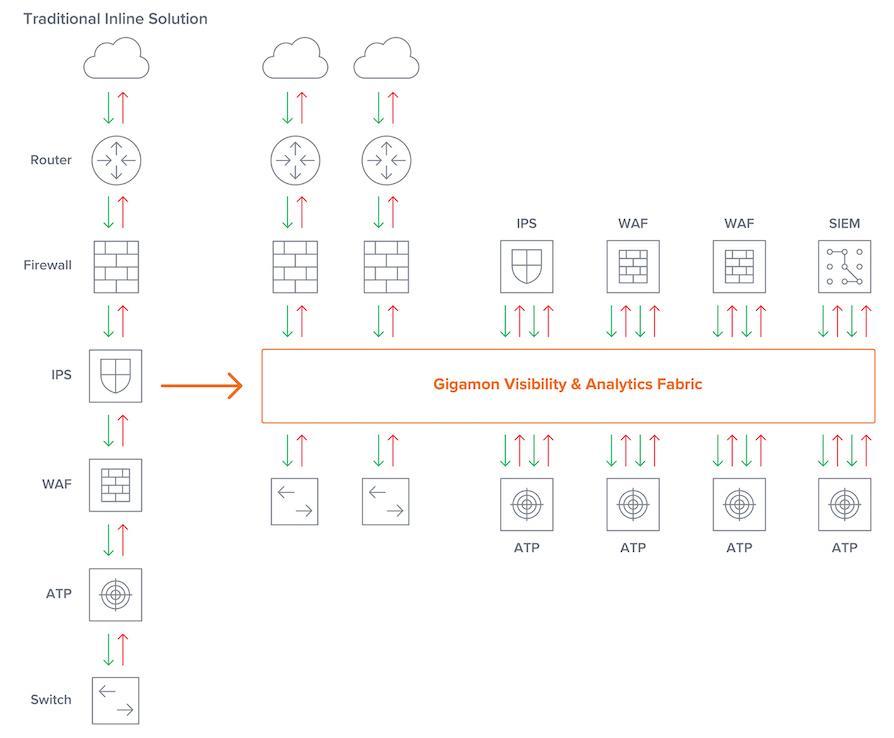
As you can see in Figure 1, with the inline bypass feature of the Gigamon NGNPB in place, inline tools can operate separated from the network, rather than in one big brittle stack connected to the network with multiple potential points of failure. And there’re lots of other neat tricks inline bypass can do as well.
Matching the Network
The separation of tools from the physical network and speed conversion lets you upgrade your network’s link speeds as you need and continue to use your existing monitoring and security tools. With multiple links in your network, oftentimes the requests and responses may follow different paths, which is known as asymmetrical routing. This is addressed by aggregation of the traffic from the links before forwarding to your tools, thus ensuring a session’s packets are put together.
The Beating of the Heart
One of the ways the Gigamon NGNPB helps keep track of each inline security tool’s operative state is by inserting small heartbeat packets into the flow of packets through each tool. By monitoring the flow through the tool, the NGNPB knows what traffic speeds look like for healthy traffic — and can immediately see when traffic suddenly slows or stops due to a problem with that tool.
In that scenario, the Gigamon NGNPB will immediately re-route network traffic to bypass the failing tool and send an alert that the tool is failing. The NGNPB itself works at wire speeds, so failover and re-routing only take milliseconds — users shouldn’t even notice when it happens. The tool can be restored to its inline position just as quickly when ready and operating optimally again.
Pick and Choose Tools
One of the downsides of a traditional inline solution is that it’s all or nothing: all your packets end up going through your whole stack of inline tools. With inline bypass, you can get a lot more selective and granular.
For instance, you could send only certain kinds of traffic through certain tools. Those tools would still work as inline tools, inspecting and signing off on every packet it receives, but they would only get the traffic they need to do their jobs; not necessarily the full firehose coming from your enterprise network. An example could be sending all traffic through an intrusion prevention system (IPS), only sending web traffic through a web application firewall (WAF), and having network detection protocols (such as ULDP) bypass all tools.
There are lots of ways you could segment traffic to different tools: For instance, you could separate traffic by specific users and server sessions, by class or type of service, by SLA requirements or geography, as specific circumstances dictate.
Handling the Volume
Even after selectively forwarding only certain traffic to specific inline security tools, there can still be far more traffic than a single instance of a tool can handle. This is where flow-aware balancing of the traffic enables you to spread the aggregate load across multiple tool ports and tool instances, ensuring packets from the same session arrive at the same tool.
Out-of-Band Tools
With inline bypass, you can pick and choose which tools are inline and which are out-of-band, and easily change things up in response to an inline tool’s performance or as your confidence in a security tool changes. For instance, you could start using a new IPS tool in passive mode to analyze out-of-band copies of traffic until you are happy with its detection capabilities, at which time you can switch it to active or inline mode and change the actual network traffic flow to pass through the IPS. You could even use different toolsets for different traffic flows at various levels of risk, monitoring copies of traffic types you feel comfortable with using out-of-band tools only, bypassing inline tools, while routing riskier traffic types through inline tools.
The Network Is the Testbed
The ability to put some tools out-of-band offers one more advantage for inline bypass: You can roll out prototypes and proof-of-concept implementations in parallel with your production environment on the same hardware and infrastructure.
Because the out-of-band tools don’t alter packets as they flow through, they won’t affect the overall network flow, but you can still see how these tools will react to your environment. This can make it easier for you to keep your tooling up to date; new toolsets (or the latest tool revisions) can be brought up in parallel with older environments, and the cutover from old production to new production environments achieved in hours, rather than weeks or months.
Long story short: Inline bypass can help you get the most of out your tooling even as you ramp up network speeds and feeds. Learn all about it at the Gigamon Inline Bypass page.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Networking group.
Share your thoughts today








