Post-Quantum Cryptography: What It Is and How It Works
Quantum computers are no longer science fiction. As these powerful machines inch closer to reality, they threaten to crack the encryption methods that protect everything from online banking to government secrets. Post-quantum cryptography offers a solution, providing security protocols designed to withstand even the most advanced quantum attacks.
So, what is post-quantum cryptography? Keep reading to learn more and get a general overview of post-quantum cryptography and how it works.
- What Is Post-Quantum Cryptography?
- Why Traditional Encryption Is at Risk
- How Post-Quantum Cryptography Works
- Real-World Applications of Post-Quantum Cryptography
- Transitioning to Quantum-Resistant Security
- Key Standards and Stakeholders in PQC
- What Organizations Should Do Now
- The Future of Post-Quantum Cryptography
- Future-Proofing Security with Post-Quantum Cryptography
- Frequently Asked Questions
Key Takeaways
- Quantum computers may be able break current encryption methods like RSA and ECC once they reach sufficient scale.
- Post-quantum cryptography uses mathematical problems that quantum computers cannot solve efficiently.
- Organizations must start preparing now for the transition to quantum-resistant security.
- NIST has already selected algorithms for standardization, providing a clear path forward.
What Is Post-Quantum Cryptography?
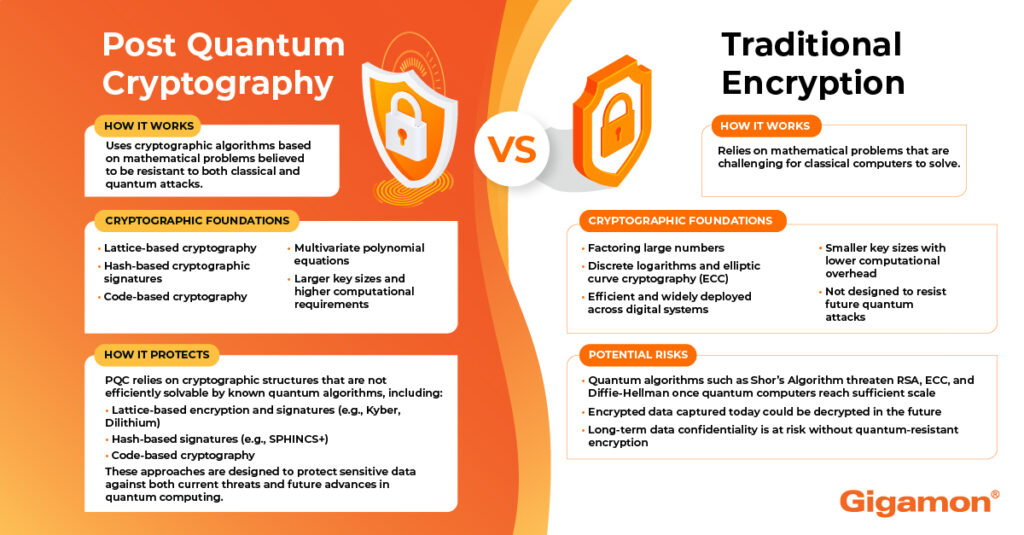
Post-quantum cryptography is a shift in digital security. Unlike traditional encryption that relies on mathematical problems classical computers find difficult to solve, post-quantum cryptography uses algorithms designed to resist quantum computer attacks.
The main difference between classical and quantum-safe encryption is computational power.
- Classical encryption depends on mathematical operations like factoring large numbers that would take classical computers thousands of years to complete.
- Quantum computers can perform these calculations exponentially faster using Shor’s Algorithm (which factors large integers) and Grover’s Algorithm (which searches unsorted databases).
Post-quantum cryptography sidesteps this problem by using mathematical structures that are difficult for computers to crack. This quantum-safe approach protects sensitive data even when quantum computers become commonplace.
Organizations must understand what the purpose of post-quantum cryptography is and how PQC optimizes security. It’s not just about future-proofing — it’s about protecting data that’s encrypted today but could be vulnerable tomorrow.
Why Traditional Encryption Is At Risk
Today’s most trusted encryption standards face an existential threat from quantum computing. RSA encryption, ECC, and Diffie-Hellman (DH) protocols depend on mathematical challenges that quantum computers can overcome. These methods have safeguarded communications for decades, but quantum computing could soon render them obsolete.
Shor’s Algorithm poses the greatest threat to current systems. This quantum algorithm can factor large integers exponentially faster than classical methods. Where a classical computer might need billions of years to crack a 2048-bit RSA key, a quantum computer using Shor’s Algorithm could break it in hours.
Organizations that fail to adopt quantum-resistant encryption before “Q-Day” — the point when quantum computers become powerful enough to break current encryption — risk exposing sensitive data to cyber attacks. Even encrypted data stored today could become vulnerable once quantum computers become powerful enough. The “harvest now, decrypt later” threat means adversaries may already be collecting encrypted data in anticipation of future quantum capabilities. So, how does PQC actually protect against quantum attacks? Let’s look at how these algorithms function.
How Post-Quantum Cryptography Works
Post-quantum cryptography relies on mathematical algorithms that fall into several families, each based on different computational challenges.
- Lattice-based cryptography: These algorithms use problems within high-dimensional structures called lattices. Even quantum computers struggle to find the shortest path through complex geometric structures, making this approach highly resistant to quantum attacks.
- Hash-based signatures: These systems rely on cryptographic hash functions that quantum computers can’t efficiently reverse. They provide provable security but come with some limitations on signature generation.
- Code-based cryptography: This approach draws strength from error-correcting codes used in telecommunications and data storage. It presents quantum computers with difficult decoding problems that remain computationally intensive.
- Multivariate quadratic equations: These algorithms challenge quantum computers with complex polynomial relationships. The mathematical complexity of solving large systems of equations provides security against quantum attacks.
The National Institute of Standards and Technology (NIST) has standardized these approaches through its post-quantum cryptography competition, selecting algorithms like Kyber and Dilithium. This process established clear guidelines for implementing quantum-resistant encryption across industries and provided the confidence organizations need to begin their transitions.
Real-World Applications of Post-Quantum Cryptography
Financial institutions, healthcare organizations, and government agencies face the greatest urgency in adopting post-quantum cryptography. These sectors handle sensitive data requiring decades of protection, making quantum-resistant encryption essential for compliance and security.
Telecommunications companies manage both data in motion and data at rest across vast infrastructures. Network visibility offered by the Gigamon Deep Observability Pipeline helps organizations monitor and secure communications while preparing for quantum-resistant implementations.
Critical infrastructure sectors rely on encrypted communications for operational technology and industrial control systems. The long operational lifespans of these systems mean encryption implemented today must remain secure for decades against future threats.
Transitioning to Quantum-Resistant Security
Organizations need crypto-agility to transition to post-quantum cryptography successfully. This ability to quickly update cryptographic algorithms makes future transitions smoother and less disruptive. Companies that build flexibility into their systems today will find quantum-resistant upgrades far more manageable.
Organizations planning their transition should follow key steps to ensure success:
- Comprehensive inventory: This includes identifying all cryptographic implementations across the organization, from obvious encryption systems to embedded cryptography in IoT devices, mobile applications, and third-party integrations.
- Risk assessment: Organizations should evaluate which encrypted data faces the greatest quantum threat. Systems protecting high-value or long-term sensitive information should receive priority for upgrades.
- Testing in controlled environments: Pilot programs help identify performance and compatibility issues before full deployment. Teams can understand the practical implications of larger key sizes and different computational requirements that post-quantum algorithms often bring.
- Gradual deployment: Organizations can implement hybrid cryptography during this phase, combining classical encryption with post-quantum algorithms. These systems provide security against both current and future threats during the transition period, though they may introduce some performance overhead.
Key Standards and Stakeholders in PQC
Multiple international organizations coordinate the global adoption of post-quantum cryptography, including:
- NIST (National Institute of Standards and Technology): This U.S. agency leads global standardization efforts through its comprehensive post-quantum cryptography competition. NIST provides the primary reference standards that organizations worldwide follow for quantum-resistant encryption.
- ETSI (European Telecommunications Standards Institute): This European organization focuses on telecommunications and network infrastructure applications. ETSI develops guidelines that complement NIST standards while addressing specific European regulatory requirements.
- ISO (International Organization for Standardization): This global standards body coordinates international compatibility of post-quantum standards. ISO ensures that quantum-resistant algorithms work consistently across borders and industries.
NIST has recommended specific algorithms that organizations can implement today:
- Kyber: This lattice-based algorithm handles encryption and key establishment with strong security properties and reasonable performance characteristics.
- Dilithium: This lattice-based digital signature algorithm provides authentication and non-repudiation capabilities for quantum-safe communications.
- SPHINCS+: This hash-based signature scheme offers an alternative approach with smaller key sizes but larger signature sizes than lattice-based methods.
The success of post-quantum cryptography depends heavily on collaboration between technology vendors, security companies, and open-source development communities. Vendors must implement standardized algorithms across diverse systems and applications, while open-source initiatives accelerate adoption by providing reference implementations and testing tools. This collaboration ensures that quantum-resistant encryption becomes accessible to organizations of all sizes.
What Organizations Should Do Now
Proactive assessment of cryptographic assets should be every organization’s first step toward quantum readiness. This inventory process consists of identifying all systems that rely on encryption, documenting the algorithms in use, and understanding the data protection requirements for each system. Many organizations discover they use encryption in more places than initially realized, from database connections to API communications.
Partnership with quantum-aware vendors provides access to expertise and solutions during the transition. Companies like Gigamon understand the challenges organizations face in implementing quantum-resistant security while maintaining network performance and visibility. These partnerships help organizations navigate technical complexities and ensure successful implementations without disrupting critical operations.
Staying informed about standardization developments helps organizations time their transitions appropriately. NIST and other standards bodies regularly update their guidance as the field evolves. Organizations should monitor these developments and adjust their implementation timelines based on new standards and emerging best practices.
Pilot programs can also be beneficial because they allow organizations to gain hands-on experience with post-quantum algorithms before full deployment. These limited-scope implementations help identify integration challenges, performance impacts, and operational considerations in controlled environments that don’t risk production systems.
The Future of Post-Quantum Cryptography
Post-quantum cryptography will evolve alongside quantum computing advances. Performance optimization is a key development area, as current algorithms often require larger keys and more computational resources than classical methods.
The integration of quantum-resistant encryption with Zero Trust architecture principles will become increasingly important. Organizations must ensure quantum-safe encryption works effectively within comprehensive security frameworks.
The evolution of cybersecurity continues as new threats emerge, including AI-powered cyber attacks that may change the threat landscape in unexpected ways.
Future-Proofing Security with Post-Quantum Cryptography
Post-quantum cryptography is a critical evolution in digital security, designed specifically to protect against the computational power of future quantum computers. These quantum-resistant algorithms use mathematical problems that remain difficult for computers to complete, ensuring long-term data protection even as computing capabilities advance.
Organizations must understand what the purpose of post-quantum cryptography is and begin their transition to quantum-resistant security now, well before “Q-Day” arrives and quantum computers gain the ability to break current encryption standards. This proactive approach protects both current data and information that must remain confidential for years or decades into the future.
Through the Gigamon Deep Observability Pipeline, organizations can:
- Map cryptographic use across hybrid and multi-cloud environments to locate systems still relying on pre-quantum algorithms and identify where PQC pilots are underway.
- Monitor PQC performance and reliability by analyzing network telemetry that reveals encrypted traffic behavior in real time, without decrypting payloads.
- Detect vulnerabilities early, such as weak cipher suites, expired certificates, and non-compliant encryption implementations.
- Optimize performance and scalability as PQC algorithms increase computational demands, ensuring that new encryption methods do not introduce latency or blind spots.
Frequently Asked Questions
Why is post-quantum cryptography important?
Current encryption methods like RSA and ECC will become obsolete once quantum computers reach sufficient power. Without quantum-resistant encryption, sensitive data remains vulnerable to future attacks, creating compliance risks and security gaps that could persist for decades.
What are the main types of post-quantum cryptographic algorithms?
Four main families provide quantum resistance:
- Lattice-based cryptography: These algorithms use complex geometric structures that quantum computers struggle to navigate efficiently.
- Code-based cryptography: This approach relies on error-correcting codes similar to those used in telecommunications and data storage.
- Multivariate polynomial equations: These systems present quantum computers with difficult polynomial solving challenges.
- Hash-based signatures: These methods build security around cryptographic hash functions that remain quantum-resistant.
Each family uses different mathematical foundations to resist quantum attacks.
Is post-quantum cryptography the same as quantum cryptography?
These are completely different technologies. Post-quantum cryptography uses traditional computing methods designed to resist quantum attacks. Quantum cryptography relies on quantum mechanics principles like quantum key distribution to detect eavesdropping attempts during communication.
How is NIST involved in post-quantum cryptography?
NIST ran a multi-year global competition to evaluate and standardize the best quantum-resistant algorithms. The competition tested dozens of proposals for security, performance, and practicality before selecting winners like Kyber for encryption and Dilithium for digital signatures.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today








 Dan Daniels
Dan Daniels