Solving the Public Sector Visibility Crisis in Hybrid Network Environments
This blog is part three of a new series on securing the modern hybrid network, “The Path to Deep Observability in the Public Sector.”
Public sector agencies today must defend increasingly hybrid, cloud-connected networks—despite constrained budgets, legacy infrastructure, tool sprawl, and rapid network growth.
The Critical Question Remains: How Do You Defend What You Can’t See?
In Greek mythology, the Graeae were three ancient sisters who shared one eye among them, with only one able to see at a time. This limited their understanding of the world and forced them to depend on a narrow and changing view, making them vulnerable and easy to outsmart. This partial and broken vision serves as a fitting metaphor for today’s hybrid cloud network environments, where security teams work with only partial visibility. Like the Graeae passing their eye to one another, organizations rely on disconnected tools, scattered data, and incomplete insights.
These visibility gaps obscure East-West lateral movement, create holes in multi-cloud visibility, slow down threat detection, and delay incident responses, leaving security teams unaware of what is happening around them. With more than 90 percent of traffic encrypted, mixed architectures, tool sprawl, and limited budgets, the situation is dire. Consequently, security teams find themselves in the dark, unable to see what is truly happening within their networks and the active threats present.
In this part three in our Public Sector Series on The Path to Deep Observability in the Public Sector,” we explore how organizations can overcome visibility challenges by shifting to visibility as a platform through Deep Observability.
Mnemosyne: Restoring Full Vision Through Deep Observability
Yet, mythology presents another character, Mnemosyne, the goddess of memory. Today deep observability plays her role, offering complete visibility across hybrid environments by capturing network-derived telemetry from physical, virtual, cloud, operational technology, Internet of Things (IoT), and mobile networks. It penetrates encrypted traffic, gathers metadata from Layers 2 to 7, and connects the details that traditional tools overlook.
With deep observability, security teams no longer need to “borrow vision” like the Graeae; they can see the entire picture in real time across each segment of the network.
The Modern Graeae Effect: Fragmented Visibility in Hybrid Networks
Like the shared eye of the Graeae, modern security infrastructures often suffer from fractured perspectives:
- Blind spots: Shadow IT, unmonitored lateral (East-West) traffic, containerized environments, and outdated systems create areas of invisibility
- Encrypted traffic: Over 90 percent of internet traffic from core to cloud is now encrypted, making traditional tools ineffective without deep traffic inspection
- Shadow AI: Unauthorized or unmonitored use of AI tools introduces new attack surfaces and data leakage risks that bypass traditional visibility and control
- Tool sprawl and underutilization: Disparate and overlapping tools create data silos, increase costs, and complicate operations while failing to provide full value or actionable insights (i.e. not seeing into encrypted traffic, or lacking lateral (East-West visibility)
- Complex environments: Hybrid and multi-cloud architectures add operational complexity, making it harder to achieve complete visibility
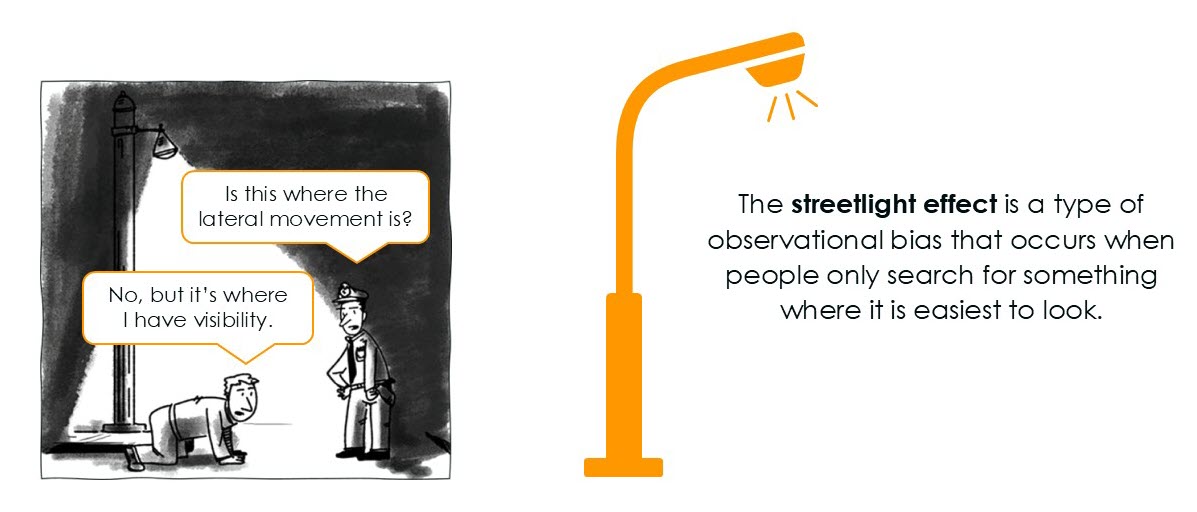
This fragmentation leaves security teams feeling reactive and vulnerable—the so-called streetlight effect in action—where you can only detect threats in the areas you can clearly see.
Mnemosyne: The Goddess of Memory and the Power of Deep Observability
Unlike the Graeae, Mnemosyne represents insight, continuity, and the ability to see everything clearly. In cybersecurity, this power is reflected in the practice of deep observability.
Deep observability replaces fragmented viewpoints with complete visibility across the hybrid-cloud network:
- Packet-level capture: Achieves complete visibility into raw traffic for forensic analysis, payload inspection, and protocol decoding, even during encrypted sessions if used with decryption
- Metadata collection: Gathers rich telemetry across Layers 2 to 7, revealing traffic patterns, application behavior, device types, and user activity without needing to decrypt data
- Correlation and enrichment: Combines data from various tools and environments to create a coherent picture, detect threats, and prioritize alerts
- Hybrid and multi-cloud coverage: Supports on-premises, virtual, cloud, operational technology (OT), and IoT environments.
With Deep Observability, organizations move from “borrowing vision” to achieving full clarity, spotting threats as they emerge.
Visibility Mandates for Modern Public Sector Defense
Recent surveys highlight the importance of this approach:
- 85 percent of cybersecurity professionals agree deep observability is essential
- 88 percent of IT and security leaders consider visibility critical for hybrid network security success
- 72 percent report that limited visibility has directly contributed to a security incident in the past 12 months
- 67 percent say blind spots in encrypted traffic are one of their top concerns for East-West threat movement
- 78 percent struggle to correlate data across multiple tools, leading to delayed detection and response
- 90 percent of organizations say hybrid environments have made security operations more complex—and visibility more challenging
From Blind Spots to Full Clarity: Four Steps to Deep Observability
- Find the Visibility Gaps Before Attackers Do
Identify blind spots across your hybrid, cloud, and legacy infrastructure to know where you are most vulnerable. - Capture What Others Miss
Collect packet-level and network-derived telemetry across every environment, including encrypted traffic. - Correlate Data and Reduce Noise
Break down tool silos and enrich data to identify threats faster and more accurately. - Continuously Adapt to Emerging Threats
Make observability an ongoing process that evolves with your environment.
Final Recommendation: Choose Mnemosyne Over the Graeae
Hybrid and cloud environments don’t have to be a mix of unclear views and blind spots. With deep observability, public sector organizations can gain Mnemosyne’s gift of memory, clarity, and control while eliminating blind spots and defending against today’s most elusive threats.
Don’t pass the eye—gain the complete view.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today
Written by Gigamon employees, assisted by AI.








