Port Spoofing: The Hidden Danger to Your Network
To paraphrase the classic public service announcement, it’s 10 p.m., do you know what’s on your network? The harsh reality is, if you’re relying on security tools that use port assignment to determine whether traffic should be inspected and by which tools, then no, you probably don’t know what’s on your network. In this blog I’ll explain some reasons why that’s so, and how Gigamon can address an emerging vulnerability.
Packets in Disguise
Let’s talk about a relatively new way that attackers are eluding detection, specifically through port spoofing.
Port spoofing is a form of network spoofing. Network spoofing describes a specific kind of cyber attack, wherein a threat actor attempts to gain access to a network by falsifying an authorized user, device, network port or computer. Through port/network spoofing once the attacker has access, they are able to easily move through your systems, compromising your vital data.
Port spoofing is a network spoof that relies on usage of non standard network TCP/UDP ports. There are lots of variations and details, but the basic idea is an attacker attempts to bypass perimeter safeguards by directing network traffic with malicious intent using non-standard (read: unexpected) ports.
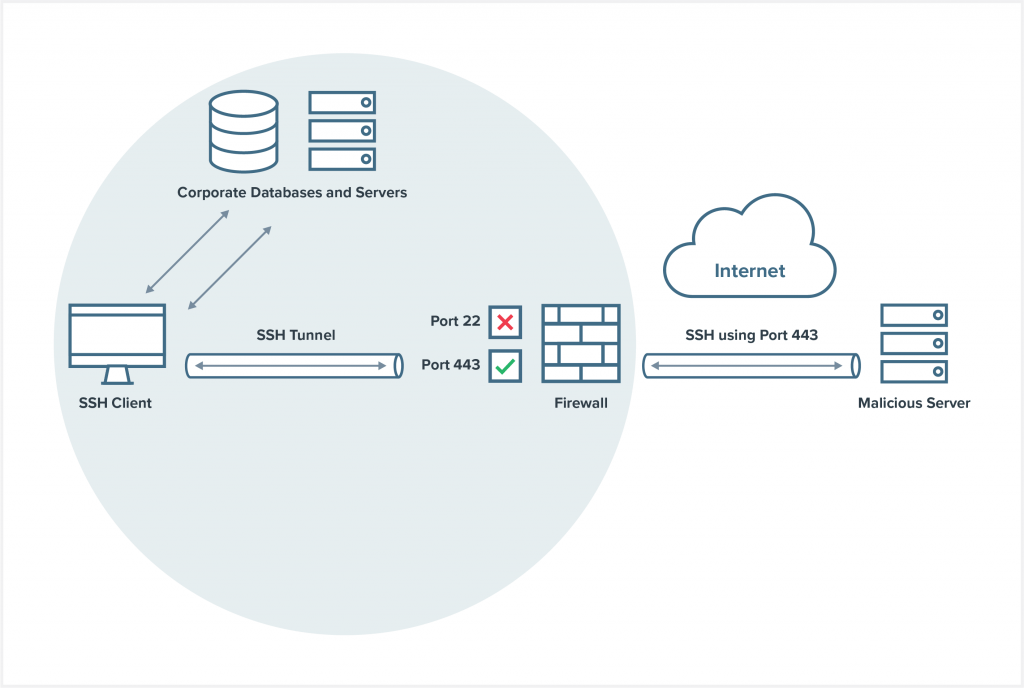
Example: Port Spoofing SSH Traffic
One of the most common and dangerous examples, which I’ll
delve into here, is spoofing secure shell protocol (SSH) traffic. SSH is
usually assigned to port 22. Security tools assume SSH traffic will use port
22, and nearly every network team in the world keeps that port thoroughly
locked down. They don’t, after all, want random outsiders starting SSH sessions
inside their networks, controlling servers and transferring files.
Done, protected. Right?
Not quite.
Not Port 22, but Port 443
What if someone spoofed their SSH traffic? Let’s say they send it to port 443 instead of port 22. Port 443 is widely used for HTTPS/SSL/TLS. HTTPS traffic is utterly ubiquitous in the modern enterprise, for both business-critical and personal activities. IT firewalls are not going to routinely block port 443/HTTPS, thus making it an ideal point of entry for attackers.
Vulnerability: Assessing Traffic by Port Only
You see the problem: If your security infrastructure determines legitimate internet traffic only by port, then it won’t notice anything unusual about these faux-HTTPS packets that could be SSH sessions harboring malware in disguise or transporting confidential data.
To add insult to injury, thinking this traffic is HTTPS, the network might even send this hostile SSH traffic to irrelevant tools in your suite (e.g., a web application firewall) that are incapable of analyzing it. If you speak a foreign language to me, I’m not going to comprehend the meaning. Similarly, when most security tools receive the wrong kind of traffic, they can’t parse it. They’ll receive SSH and treat it as HTTPS, shrugging and saying “I don’t know what this is” before proceeding to ignore it.
SSH: It’s Calling from Inside the House
That’s bad because SSH is one of the riskiest protocols an organization could allow in.
How bad? A malicious actor could use spoofing to create an SSH client inside the corporate network, setting it to listen to a certain external port. Then it’s a simple matter to send commands to it via an external command-and-control server. The attacker can do all kinds of damage, whether that’s to plant malware, exfiltrate files or even redirect internal database queries to an external database under their control, with none the wiser.
Another attacker could bribe a member of the cleaning staff to hide a Raspberry Pi under the floor and connect it to the network. IT notices an uptick of “SSL” traffic to a certain IP address but, hey, that’s web services stuff, so absent greater insight from security tools, they just assume the developers are working on some project and leave it at that. Again, the attacker has carte blanche to do as they wish.
This could be happening right now. If your monitoring tools aren’t smart enough to look beyond superficial signifiers like destination port, how would you know?
You Can’t Hide from Deep Packet Inspection
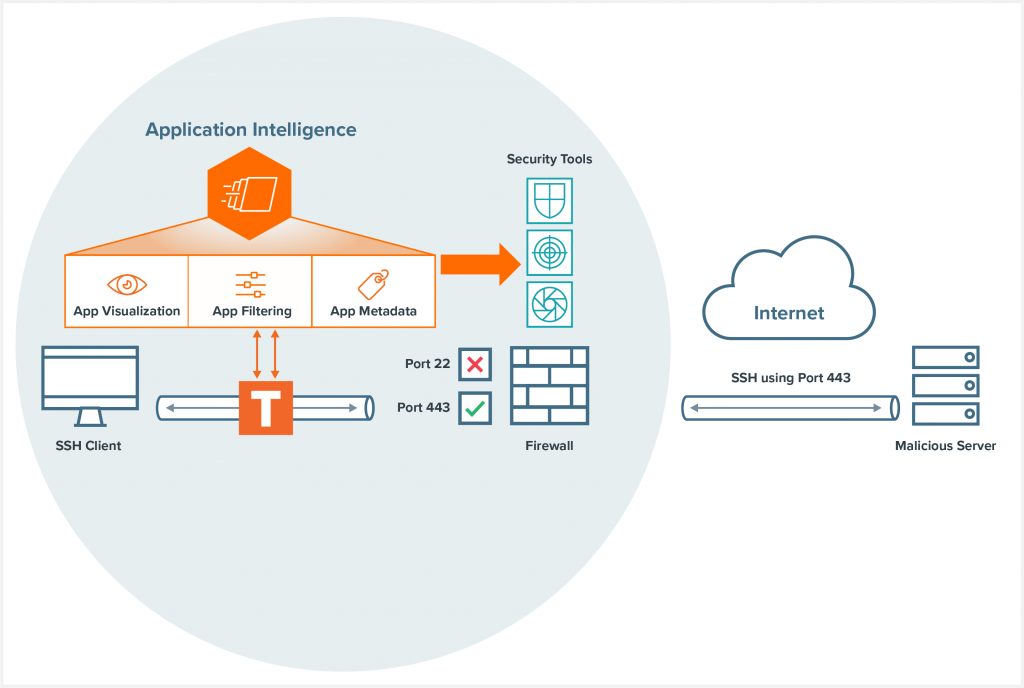
It’s not enough to merely monitor for traffic going to and from ports; you need insight into what that traffic actually is — an ability to look beyond the port number, using deep packet inspection (DPI) to correctly identify applications and protocols. At Gigamon, we refer to this as application intelligence.
Gigamon recently introduced Application Filtering Intelligence, which identifies more than 3,000 common business and consumer applications using deep packet inspection. Application Filtering Intelligence doesn’t just look at the outer headers, it also looks deeper into the packet. We look deep into the unique characteristics of the packet that define a given application.
In the case of port spoofing, Gigamon can alert you to the fact that camouflaged SSH application traffic was being sent through port 443. Then it’s easy to address, whether that means updating rules to block this traffic or some other form of remediation. The bad actor can try spoofing to any port they want, but every time Gigamon Application Filtering Intelligence will correctly identify it.
Unfortunately, attackers are continually evolving their tactics. It’s likely that attackers will move onto other vectors once they realize organizations are onto their port spoofing game. Gigamon is committed to helping you better monitor and control network traffic, so you’ll be ready for what comes next.
Learn More
To learn more about how application awareness can help your organization, check out our Application Filtering Intelligence page, and remember, sometimes innocuous-looking packets could just be a wolf in HTTPS clothing.
Featured Webinars
Hear from our experts on the latest trends and best practices to optimize your network visibility and analysis.

CONTINUE THE DISCUSSION
People are talking about this in the Gigamon Community’s Security group.
Share your thoughts today