Accelerating Digital Transformation Through Application Intelligence
Many of us are familiar with Darwin’s theory of evolution that professed continuous incremental change as the cause for evolution of new species. Gould and Eldredge, on the other hand, talked about a slightly different model that had longer periods of equilibrium or relative stasis, punctuated by periods of rapid change. At the end of the rapid change, species had evolved considerably, or entirely new species had evolved. And this would be followed by another period of relative equilibrium.
Digital transformation (DX) is driving exactly such a period of punctuated rapid change across multiple industries. From the automobile sector with autonomous and semi-autonomous capabilities, to music and video distribution via streaming, to Robotic Process Automation (RPA), new companies are taking leadership roles, creating entirely new industries, and pressuring older companies to adapt and evolve or fade away.
To be sure DX is a business imperative. It is about transforming user experiences, driving operational efficiencies across internal processes and fundamentally transforming business models. DX leverages digital technologies we are familiar with, such as 100GB networks; high-speed Wi-Fi; machine learning (ML); artificial intelligence (AI); private, public and hybrid clouds; as well as increasingly leveraging connected devices for operational technologies (OT).
At the heart of DX are new digital applications that are powering the transformation. These new digital applications are built using microservices architectures and scale out models, and heavily leverage open source and cloud technologies.
A key challenge that arises when dealing with this new breed of digital applications is their complexity, which ultimately manifests itself as challenges around securing the applications, as well as ensuring consistent performance and experience. Application complexity is growing rapidly due to several factors:
- Applications today are moving towards a microservices architecture: The microservices are written by different developers, some in-house, some outsourced. Additionally, many of these microservices leverage a combination of open source, commercial and in-house proprietary technologies. This significantly increases the attack surface and threat envelope, especially given the multitude of in-house and external sources that contribute to building the application.
- Infrastructure complexity: Today’s digital applications run across a variety of infrastructure, from on-premise bare metal servers, to private clouds to public cloud IaaS-, PaaS- and SaaS-based components. Understanding application and application component access patterns to accomplish micro segmentation across such a distributed paradigm poses risk in terms of accurately controlling and monitoring access, but also accidental service outages due to the underlying complexity.
- The increasing use of connected devices: This is a particularly concerning issue. While the productivity benefits are significant, the risks and threats are equally or more significant. In the world of connected devices, cyber-attacks move from attacks on data to attacks on flesh, blood and steel. And they move from attacks on confidentiality of data to attacks on availability and integrity of systems. This is a very different risk rhetoric than we are used to today.
An essential step to address some of these issues is understanding what applications and microservices are running across your hybrid infrastructure, along with a simple way to visualize that. Once done, the ability to isolate specific applications or microservices communication streams for deeper inspection would allow the security operations to easily understand access patterns and put in place effective micro segmentation strategies.
Application developers too can benefit from this by better understanding communication bottlenecks between applications and microservices, as well as troubleshoot applications and microservices. Finally, the ability to extract metadata pertaining to those applications or services of interest can then fill gaps from a compliance and risk mitigation strategy.
Today, Gigamon is announcing our Application Intelligence framework that addresses many of the above considerations.
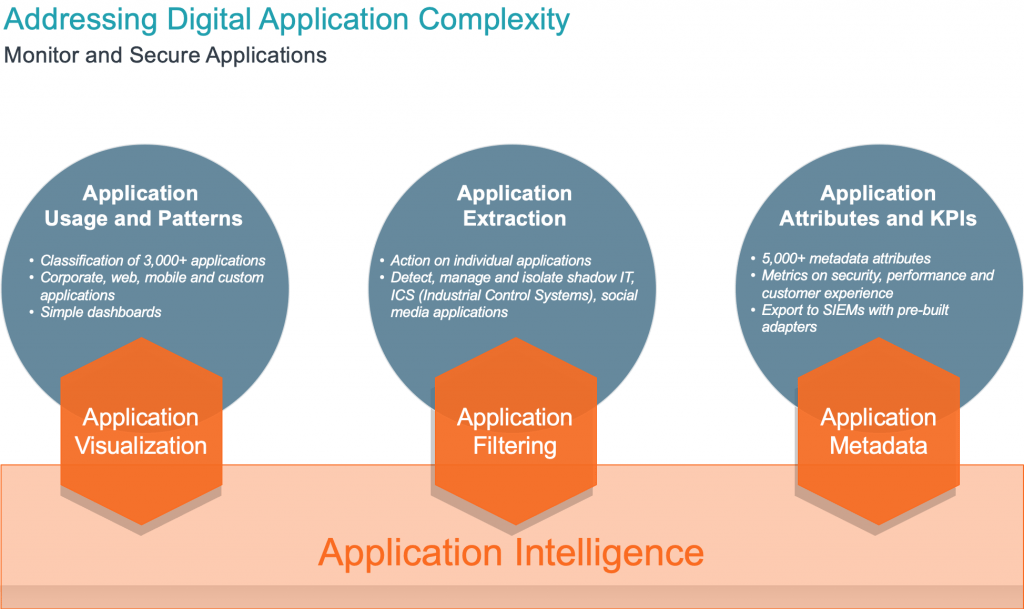
The Gigamon Application Intelligence framework provides a way to instantly identify and visualize more than 3,000 applications out of the box. It provides the ability to target specific application streams for deeper inspection without having to deal with IP addresses, L4 ports or other networking constructs; but rather deal with applications directly at the application level. It will also have the ability to extract more than 5,000 metadata elements from the application streams and feed them into SIEMs, such as Splunk and QRadar, using pre-built adapters or into other collectors such as IPFIX collectors. The applications and metadata elements cover many enterprise and web applications and protocols, as well as protocols and applications commonly used with connected devices for OT.
Application-centric visibility is key to accelerating digital transformation. By better visualizing, isolating and understanding application interaction and usage patterns, organizations can accelerate deployment of their digital applications. For more information, please visit gigamon.com.
Continue the Discussion
People are talking about this in the Gigamon Community’s
Application Intelligence group. Share your thoughts today.









