Seven Commandments and Two Sins of SSL Decryption
The Seven Commandments
1. Know Thy Traffic
First, before deploying any SSL decryption solution, be aware of the total volume of traffic in your network and the amount of traffic that is SSL encrypted. A good free tool is NTOPNG, which can give you insight into your network.
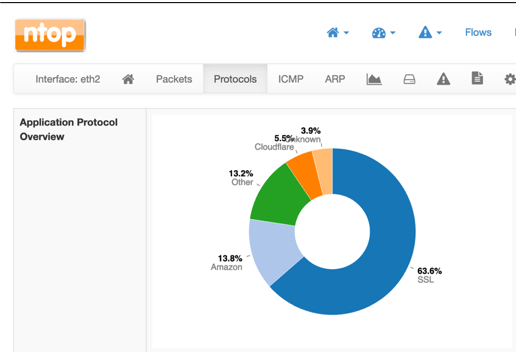
Second, know how and where your traffic is traversing the network. For an SSL solution to work flawlessly, it needs to see both directions of the traffic. Asymmetric traffic can cause incomplete SSL decryption if all traffic is not combined and fed to the solution.
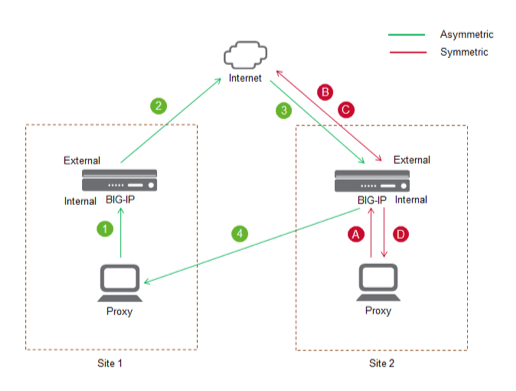
2. Know Thy Direction
It’s important to know which traffic needs to be decrypted. Either you’re hosting on-premises web applications that are accessed internally or externally, or you want to decrypt all the traffic leaving your network.
Each case requires different techniques for on-premises web applications. In the first scenario, you’ll need a private key for decryption; for outbound traffic only, you’ll need to use man-in-the-middle (MITM) decryption.
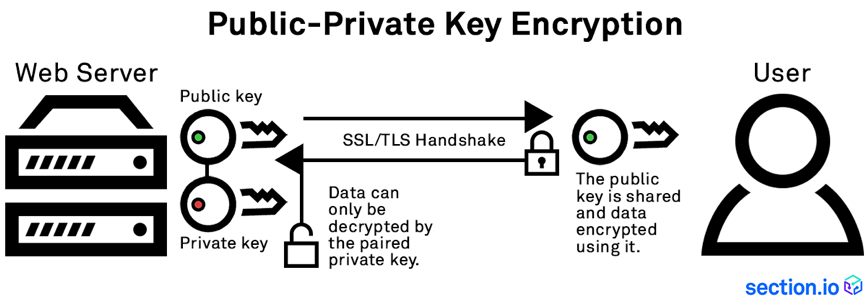
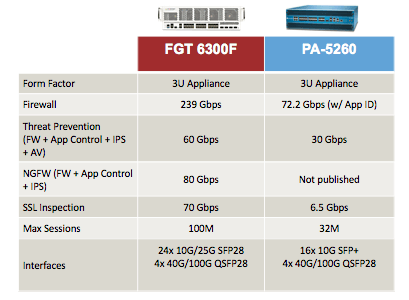
3. Know Thy Limits
Different solutions offer different SSL decryption capacity for inbound or outbound traffic. It’s important to know how much traffic can be decrypted by a solution based on the active number of connections and volume of SSL traffic.
4. Know Thy Needs
Once you have traffic decrypted, where do you need to steer that traffic? Does just one tool need to see decrypted traffic, or multiple tools?
5. Know Thy Priorities
Many security tools and firewalls offer an SSL decryption solution, but that sometimes impairs their primary function. In these cases, enabling SSL decryption can cause high CPU usage, degrading the tool’s ability to inspect or block traffic.
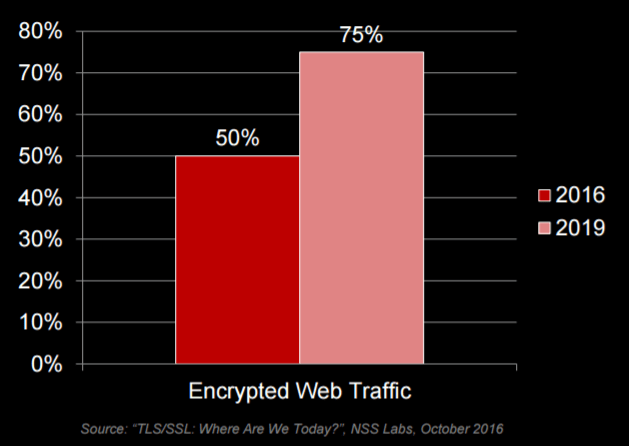
According to NSS Labs Test Reports,1 there was a 92 percent drop in the average connection rate of the products that perform SSL decryption, with connection degradation from 84 percent to 99 percent.
- Latency in the average application response time of the tested products increased by 672 percent, with latency ranging from 99 percent to 2,910 percent
- There was a 60 percent drop in the average throughput of the tested products, with throughput degradation ranging from 13 percent to 95 percent
- Not all tested products support the top 30 cipher suites of the Alexa Top 1 Million (as of December 31, 2017)
- Some tested products support emergent ciphers
6. Know Thy Growth
SSL decryption may be easy to configure for your current setup, but what happens if your traffic volume grows? How easy it would be to scale your SSL decryption solution over time, and what would be the cost impact?
7. Know Thy Solutions
Do your research when deploying SSL decryption solutions. Different solutions offer varied performance with different ciphers. Some solutions are easier to deploy or scale better than others. Thoroughly research available solutions and their pros and cons.
And the Two Sins
1. Thou Shall Not See What’s Not Meant to Be Seen
While seeing all decrypted traffic may be good for security, decrypting financial and health data violates privacy laws. The solution must have the ability to distinguish data that needs to be decrypted from data that shouldn’t be decrypted.
2. Thou Shall Not Cause Outages
No matter how much a solution is tested in a lab environment, the production environment is different. The solution should be easy to bypass in the event of a catastrophe.
Continue the Discussion
People are talking about this in the Gigamon Community’s
Security group. Share your thoughts today.
1. NSS Labs. “NSS Labs Expands 2018 NGFW Group Test with SSL/TLS Security and Performance Test Reports.” AP News. July 24, 2018. Accessed April 23, 2019. https://www.apnews.com/b1f6dad7186f119dae4e150ba7d419e4.









