Prevent Security Tool Downtime with Inline Bypass Threat Prevention
Updated October 28, 2021.
Challenge
Today’s networks are transforming at an exponential pace with higher data volumes, faster network speeds and of course newer threat vectors. Now add to that the complexity that virtualized and public cloud environments bring. So how do security and networking professionals work together to provide the best security without impacting network performance? Oftentimes they are forced to pick one over the other.
To effectively monitor today’s network infrastructures, organizations are deploying a plethora of security solutions. Although this approach may seem best, it leads to multiple points of possible network failure, degradation of network and application performance, and a lack of scalability, to name just a few drawbacks.
Solution: Deploy a Network Packet Broker
One way to maintain network performance is to deploy a next generation network packet broker that includes an inline bypass protection solution. Inline bypass acts as a fail-safe access port for inline security tools, such as web application firewall (WAF), intrusion prevention system(IPS), and advanced threat protection (APT) solutions.
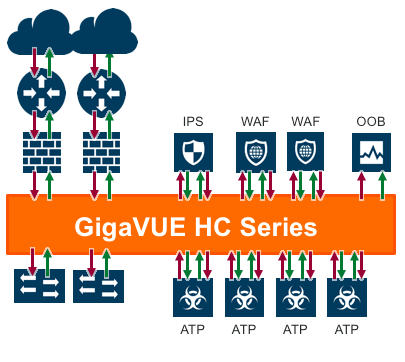
Inline Bypass with the GigaSECURE Security Delivery Platform
We have recently added key enhancements to the Inline Bypass feature in the GigaSECURE® Security Delivery Platform (GigaSECURE). Among these enhancements, GigaSECURE now supports flexible inline arrangements, which optimizes inline traffic flows for ingress and egress. With this improved usability, you can now:
- Overcome physical deployment obstacles by resolving media and speed mismatches and add, remove and upgrade tools without network disruption.
- Maximize network availability by protecting against network failures and applying multi-tool resiliency.
- Improve network and application performance by controlling what traffic goes to which tools.
- Increase the scale of security inspection by protecting multiple network links with the same tools and distributing traffic across multiple tool instances.
Secure asymmetrically routed traffic by forwarding session traffic to the same tools regardless of network link.
Business Benefits
With these enhancements, GigaSECURE enables organizations to take advantage of a resilient, scalable and simplified architecture that:
- Maximizes tool efficiency.
- Scales at the speed of the network.
- Removes single points of failure.
- Improves operational agility as security operation teams can seamlessly add, remove and upgrade tools and dynamically send suspicious flows to tools for analysis or quarantine.
- Helps bridge the gap between SecOps and NetOps.
Now that sounds like something that will help security professionals sleep better at night.
To learn more please visit the Inline Bypass page.








