Gain Visibility and Automate Threat Hunting in the Cloud with Gigamon and Vectra
As enterprises migrate to the cloud, strong perimeter defenses are not enough to stop cyber attackers from infiltrating the network. Together, Gigamon and Vectra enable organizations to gain network visibility and automate threat management – providing continuous monitoring of network traffic to pinpoint cyber attacks that evaded perimeter defenses.
Chris Morales, Head of Security Analytics at Vectra joins us to discuss what challenges he sees customers facing when moving to Amazon Web Services (AWS) and how Gigamon and Vectra can help them.
Could you tell us a little bit about Vectra?
Vectra is an artificial intelligence company transforming cybersecurity with the Cognito platform that automates threat hunting. Vectra Cognito is a software solution that is the fastest, most efficient way to find and stop attackers inside your network. Cognito automates the hunt for cyber attackers, shows where they’re hiding and tells you what they’re doing. The highest-risk threats are immediately prioritized so security teams can respond faster to stop in-progress attacks and avert data loss.
What kind of challenges are you seeing from customers who are moving to the public cloud?
Cloud security should not simply consist of a perimeter solution deployed in the cloud. Joint research from Microsoft and the University of Wisconsin shows that 80% of traffic stays inside the data center. Cloud data centers encounter threats in the more advanced phases of the attack lifecycle.
Perimeter technology is specifically focused on detecting the initial compromise or infection (e.g., exploits and malware) but is ineffective if attackers manage to get onto the network. Today’s attackers are far more likely to infect hosts within the enterprise, escalate their level of trusted access, and use their position of trust to pivot into the cloud to steal or damage critical assets.
Administrative accounts and protocols can give attackers backdoor access into the cloud without the need to directly exploit an application vulnerability. By using standard admin tools such as SSH, Telnet or RDP, attackers can easily blend in with normal admin traffic.
Since these secondary phases of attack use allowed protocols and don’t rely on malicious payloads, it is important to use behavioral models to detect malicious actions. Applying behavioral models to real-time network traffic works best – the alternative is to use flow logs, but these are not available for all the protocols that could be used (e.g., IPMI), and are often sent in batches rather than in real-time, allowing the attacker time to erase logs.
In addition, cloud environments are always in flux. The dynamic and agile nature of the cloud is one of its most attractive qualities. Developers can quickly spin up new applications and have access to live production data for testing. So your security solution needs to be able to handle this dynamism as well.
Finding attacker behaviors and tracking the progression of an attack requires visibility across each part of the network, regardless of the underlying technology. When it comes to cybersecurity, it isn’t enough to just deploy a virtual version traditional security tools as a workload in the cloud, you need to be able to cover your complete environment to maximize your defensive effectiveness.
Can you tell us a bit about your cloud capabilities and the benefits for our mutual customers deploying applications on AWS?
Vectra Cognito can examine all traffic into, within and out of AWS in order to detect attacker behavior. Cognito pays special attention to administrator credentials and administrative protocols while modeling the administrators for specific resources or workloads in the cloud, as well as what tools they use.
Cognito recognizes rogue administrators and suspicious use of administrative protocols, and alerts security teams to potentially compromised cloud workloads and databases. Likewise, Cognito detects regular end-users who suddenly begin using administrative access and protocols. These detections come with the context of the normal administrator and protocols used on these workloads so analysts can quickly evaluate the abnormal behavior.
How does Vectra integrate with Gigamon on AWS?
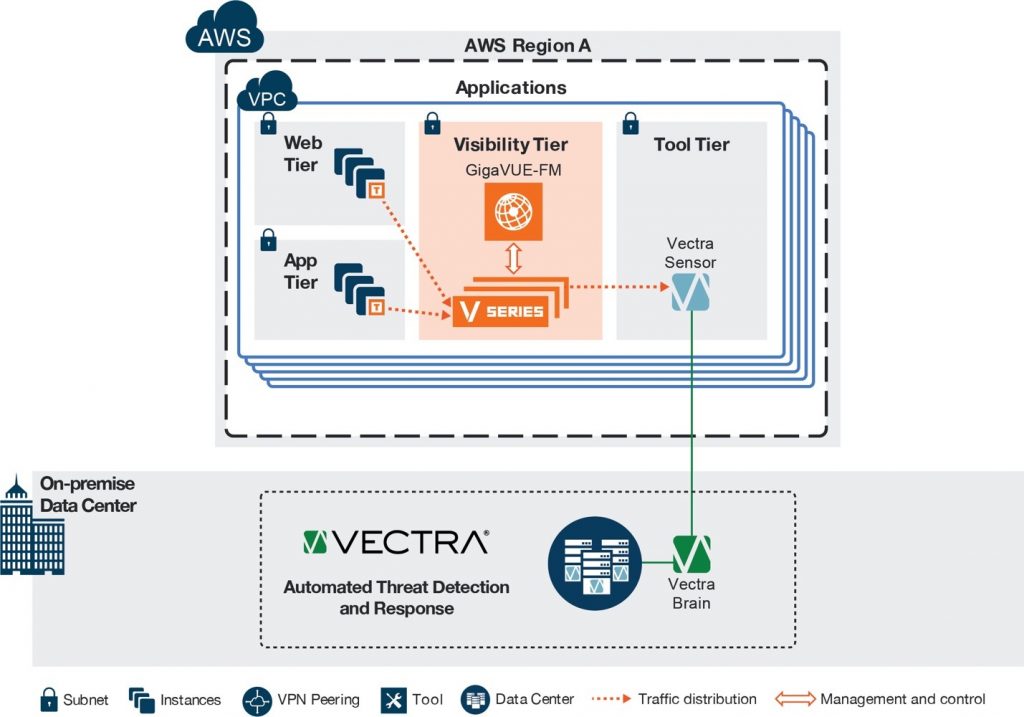
Gigamon provides our customers with an excellent way to see the traffic flowing within their AWS environment. The Gigamon Visibility Platform for AWS has extended our integration with Gigamon to ensure coverage of our customers’ networks across physical, virtual and cloud technologies.
Within AWS, the Gigamon solution delivers all network traffic to Vectra efficiently and in the correct format allowing us to monitor internal (east-west) cloud and virtual traffic. With their lightweight G v-TAP agent to copy cloud traffic and send it to Vectra Cognito via the V Series visibility nodes we can eliminate blind spots and ensure all traffic is monitored and analyzed together.
How can readers learn more?
You can register to watch the on-demand joint webinar.
For more information on the Joint Gigamon-Vectra partnership, please watch our video featuring Chris Morales.