SC16 – What an Experience!
 For the third year in a row, Gigamon and I have been actively participating in Super Computing’s network or SCinet. As Allen Hebert noted in his blog last year about SC15, the annual conference is “more than just experts giving talks, more than vendors trying to sell; it is a collaboration among peers who are seeking to push the limits of computing and networks”.
For the third year in a row, Gigamon and I have been actively participating in Super Computing’s network or SCinet. As Allen Hebert noted in his blog last year about SC15, the annual conference is “more than just experts giving talks, more than vendors trying to sell; it is a collaboration among peers who are seeking to push the limits of computing and networks”.
SC16 hosts the most powerful and advanced network in the world – SCinet. Created each year for the conference, SCinet brings to life a very high-capacity network (5 service providers provisioning over 3.15 Tbps, 200 wireless access points, over 30 classrooms) that supports the revolutionary applications and experiments that are a hallmark of the SC conference. SCinet will link the convention center to research and commercial networks around the world. In doing so, SCinet serves as the platform for exhibitors to demonstrate the advanced computing resources of their home institutions and elsewhere by supporting a wide variety of bandwidth-driven applications, including supercomputing and cloud computing.
SCinet infrastructure is designed and delivered by volunteers from academia, government, and industry all working together. Industry vendors and carriers donate millions of dollars in equipment and services needed to build and support the local and wide area networks. Planning begins more than a year in advance of each SC conference and culminates in a high-intensity installation in the days leading up to the conference.
What Was Gigamon’s Role at SCinet?
Gigamon provided pervasive visibility into data-in-motion for network security purposes. SCinet is literally on the Internet without any borders as the network is designed to provide high-performance communications, and security tools such as firewalls can be viewed as inhibitors to achieving the highest speeds. Given the above, the network security team is charged with three main objectives:
- Protect SCinet from the world – make sure that the attendees, exhibitors, and vendors are safe from external attacks
- Protect the world from SCinet – prevent unconscious side effects, exiting SCinet
- Ensure security inside the network
In essence, our activities included blocking malicious hosts, detecting and preventing compromised systems, and mitigating the effects of compromised systems.
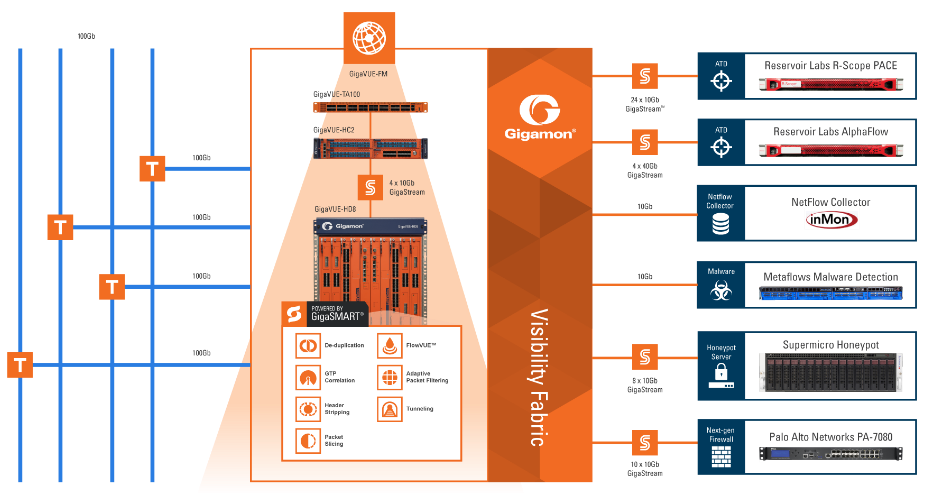
To achieve our goals, Gigamon products provided complete visibility and control of traffic in support of the security tools. We first passively tapped the external Internet connectivity (four 100Gbps and three 10Gbps links) of SCinet. The 100Gbps links were forwarded to a GigaVUE-TA100 Visibility Fabric node, while the 10Gbps links terminated on the HC2 embedded TAPs. The Visibility Fabric nodes provided a set of key services for delivery of data to the tools, including packet filtering, packet replication, packet load balancing, as well as GigaSMART® packet transformation, such as packet deduplication and header stripping to remove duplicate packets or normalize the traffic (remove all VLAN information).
For threat analysis, in addition to traffic coming from the Internet, another 38 exhibition and classroom 1Gbps and 10Gbps links were tapped and that traffic was shared with several different tools: Reservoir Labs R-Scope and AlphaFlow security appliances, Palo Alto Networks PA-7080 Next Generation Firewall (NGFW), a honeypot and a MetaFlows malware detection appliance. Ingress traffic was assigned a VLAN tag based on the port it came on, allowing for better spatial location when we needed to find someone or something in the network.
Traffic was passed to the tools as follows:
- Reservoir Labs R-Scope (Advanced Threat Detection) – 24 load-balanced, 10Gbps ports
- Reservoir Labs AlphaFlow – 4 load-balanced, 40Gbps ports
- Palo Alto NGFW – 10 load-balanced, 10Gbps ports
- Honeypot server – 16 load-balanced, 10Gbps ports
- MetaFlows (malware detection) – one 10Gbps port. Since the amount of network traffic was much larger than the effective ingest of the MSS-64C appliance, we were heavily filtering it, passing only ports 1-1079, 1081-5000, and 8080-8088 as well as removing the any VLAN tags.
Lastly, and in parallel to the raw packet stream processing, GigaVUE-HD8 filtered, aggregated, and forwarded select traffic for unsampled 1:1 NetFlow generation, delivered to inMon’s Traffic Sentinel and Gigamon’s FabricVUE Traffic Analyzer.
In addition to working with our tools in a real, high-speed network (something I don’t get to do very often), I had the opportunity to work with some of the coolest folks from government, academia, and partner companies. We worked on real-world security issues, utilizing state of the art tools. More importantly, I got to witness the difference my product makes on the abilities of these security professionals.
About SC16
SC16, sponsored by ACM (Association for Computing Machinery) and IEEE Computer Society offers a complete technical education program and exhibition to showcase the many ways high performance computing, networking, storage and analysis lead to advances in scientific discovery, research, education and commerce. This premier international conference includes a globally attended technical program, workshops, tutorials, a world class exhibit area, demonstrations and opportunities for hands-on learning. For more information on SC16, please visit http://www.sc16.supercomputing.org/, or contact [email protected] for more information.